What is this feature called?
Cisco firewalls and routers can respond to a TCP SYN packet that is destined for a
protected resource, by using a SYN-ACK packet to validate the source of the SYN packet.
What is this feature called?
Which set of commands is required on an ASA to fix the problem that the exhibit shows?
Which statement about the Cisco Secure Desktop hostscan endpoint assessment feature is true?
Which statement about the Cisco Secure Desktop hostscan endpoint assessment feature
is true?
Which of these is the appropriate configuration on the Cisco ASA adaptive security…?
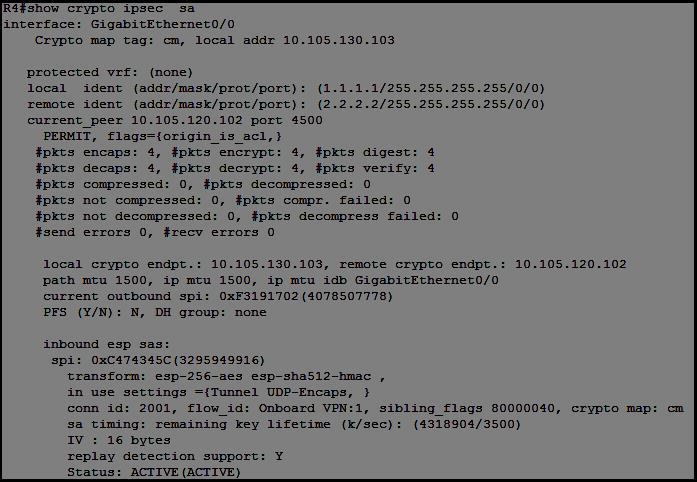
Refer to the exhibit.
Client1 has an IPsec VPN tunnel established to a Cisco ASA adaptive security appliance in
Chicago. The remote access VPN client wants to access www.cisco.com, but split
tunneling is disabled. Which of these is the appropriate configuration on the Cisco ASA
adaptive security appliance if the VPN client’s public IP address is 209.165.201.10 and it
is assigned a private address from 192.168.1.0/24?
Which port is used by default to communicate between VPN load-balancing ASAs?
Which port is used by default to communicate between VPN load-balancing ASAs?
Which three statements apply to the behavior of Cisco AnyConnect client autoreconnect?
Which three statements apply to the behavior of Cisco AnyConnect client autoreconnect? (Choose three.)
What could be the potential problem?
You are trying to set up a site-to-site IPsec tunnel between two Cisco ASA adaptive
security appliances, but you are not able to pass traffic. You try to troubleshoot the
issue by enabling debug crypto isakmp and see the following messages:
CiscoASA# debug crypto isakmp
[IKEv1]: Group = 209.165.200.231, IP = 209.165.200.231, Tunnel RejecteD. Conflicting
protocols specified by tunnel-group and group-policy
[IKEv1]: Group = 209.165.200.231, IP = 209.165.200.231, QM FSM error (P2 struct
&0xb0cf31e8, mess id 0x97d965e5)!
[IKEv1]: Group = 209.165.200.231, IP = 209.165.200.231, Removing peer from
correlator table failed, no match!
What could be the potential problem?
which step should the stakeholder be involved?
When you work on a change-management process, you generally identify potential
change, review the change request, implement change, then review the change and
close the process. In which step should the stakeholder be involved?
which four areas is coverage most important?
Many guidelines can be used to identify the areas that security policies should cover. In
which four areas is coverage most important? (Choose four.)