Which three statements describe the security weaknesses of WEP?
Which three statements describe the security weaknesses of WEP? (Choose three.)
what are three benefits of using the TKIP instead of WEP?
When implementing WLAN security, what are three benefits of using the TKIP instead of
WEP? (Choose three.)
Which three nonproprietary EAP methods do not require the use of a client-side certificate for mutual authenti
Which three nonproprietary EAP methods do not require the use of a client-side
certificate for mutual authentication? (Choose three.)
Which option explains the passive scan technique that is used by wireless clients to discover available wirele
Which option explains the passive scan technique that is used by wireless clients to
discover available wireless networks?
Which message could contain an authenticated initial_contact notify during IKE main mode negotiation?
Which three statements are true?
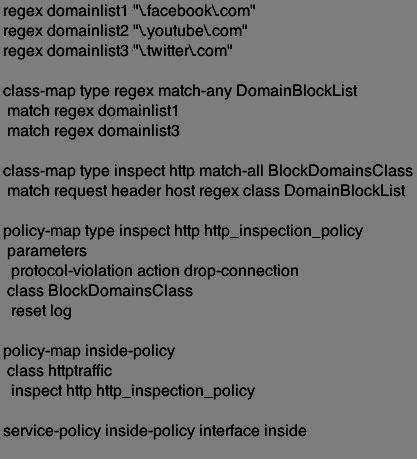
What will be the default action?
Which Cisco ASA feature can be used to update non-compliant antivirus/antispyware definition files on an AnyCo
Which Cisco ASA feature can be used to update non-compliant antivirus/antispyware
definition files on an AnyConnect client?