Which of the following commands could be used to preven…
The conference room has a switch port available for use by the presenter during classes. You would like to prevent that port from hosting a hub or switch.
Which of the following commands could be used to prevent that port from hosting a hub or switch?
Which of the following are NOT valid IPv6 addresses?
Which of the following are NOT valid IPv6 addresses? (Choose all that apply.)
Which WAN switching technology is used with ISDN?
Which WAN switching technology is used with ISDN?
What Cisco IOS command produced the following as a part…
What Cisco IOS command produced the following as a part of its output?
Port Security: Enabled
Port status: SecureUp
Violation mode: Shutdown
Maximum MAC Addresses: 2
Total MAC Addresses: 2
Configured MAC Addresses: 2
Aging Time: 30 mins
Aging Type: Inactivity
SecureStatic address aging: Enabled
Security Violation count: 0
What would be the advantages of using Point to Point Pr…
You are configuring a serial link between a Cisco router and a router produced by another vendor. What would be the advantages of using Point to Point Protocol
(PPP) over High Level Data Link Control (HDLC) in this scenario?
Which of the following are classless routing protocols?
Which of the following are classless routing protocols? (Choose four.)
Which of the following commands helps you determine the…
Which of the following commands helps you determine the Layer 1 and Layer 2 up/down status of a Cisco interface?
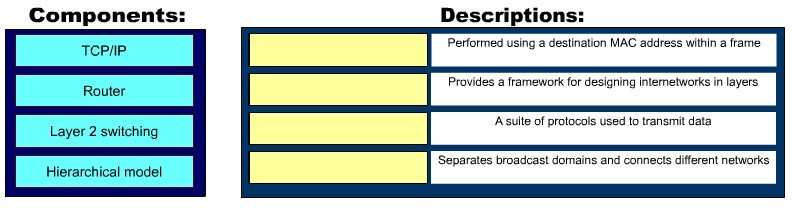
Click and drag the network components and functions to…
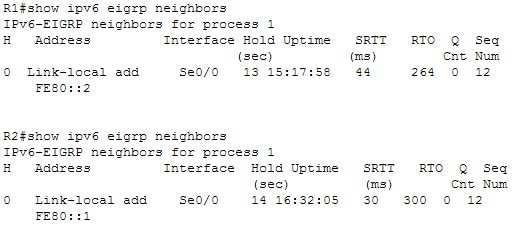
What is true of this configuration?
What is the possible IP range that can be assigned to h…
What is the possible IP range that can be assigned to hosts on a subnet that includes the address 192.168.144.34/29?