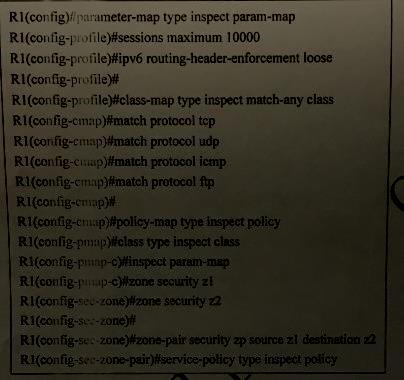
Which two statements about the given IPv6 ZBF configuration are true?
Which two statements about DTLS are true?
Which two statements about DTLS are true?(Choose two.)
What protocol does SMTPS use to secure SMTP connections?
What protocol does SMTPS use to secure SMTP connections?
What security element must an organization have in place befor it can implement a security audit and validate
What security element must an organization have in place befor it can implement a
security audit and validate the audit results?
Which two router configurations block packets with the type 0 routing header on the interface?
What are three ways you can enforce a BCP38 policy on an Internet edge device?
What are three ways you can enforce a BCP38 policy on an Internet edge device?
(Choose three.)
What feature must be implemented on the network to produce the given output?
Which two values must you configure on the Cisco ASA firewall to support FQDN ACL?
Which two values must you configure on the Cisco ASA firewall to support FQDN
ACL?(Choose two.)
What is an example of a WEP cracking attack?
What is an example of a WEP cracking attack?
Which statement about remote procedure calls is true?
Which statement about remote procedure calls is true?