How does PEAP protect the EAP exchange?
How does PEAP protect the EAP exchange?
Which command verifies the digits that are received by voice-port?
A voice engineer is troubleshooting an issue that involves incoming calls to POTS lines. Which command
verifies the digits that are received by voice-port?
How does a zone-based firewall implementation handle traffic between interfaces in the same zone?
How does a zone-based firewall implementation handle traffic between interfaces in the same zone?
Which dial plan type should the engineer recommend?
An engineer is designing a new dial plan for a customer that has offices in several countries on four
continents around the world. This client also wants to integrate with a Microsoft Lync backend. Which
dial plan type should the engineer recommend?
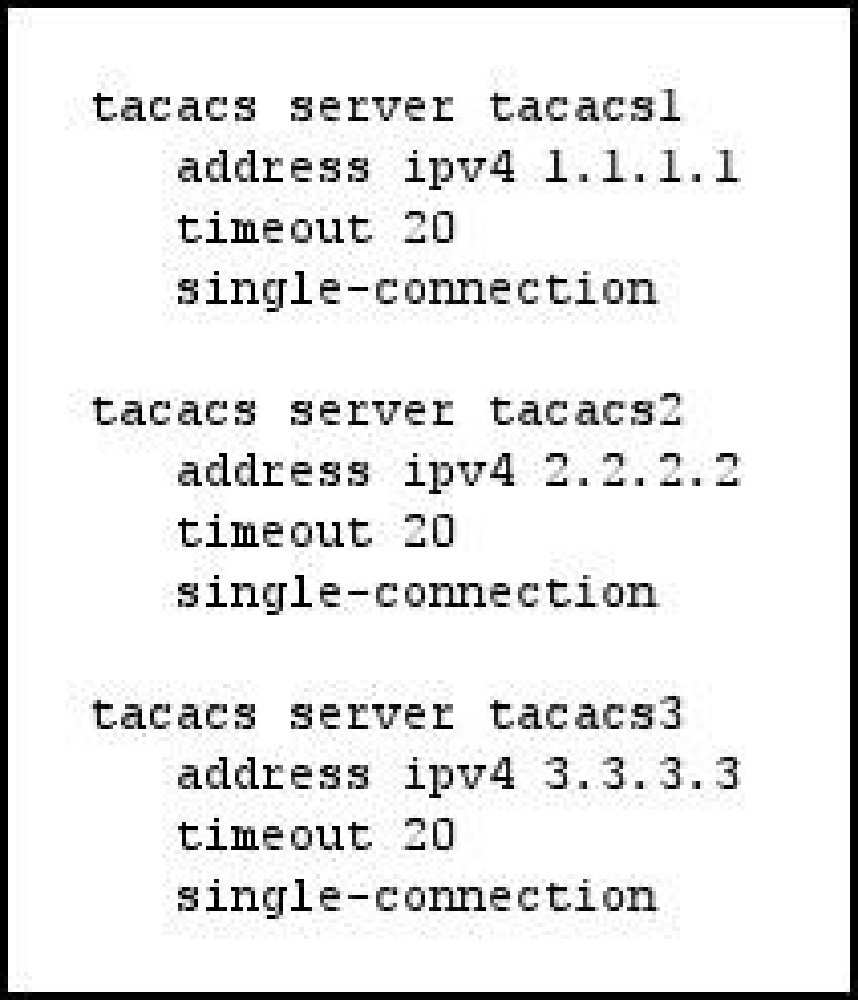
Which statement about the given configuration is true?
Which two pieces of information can be determined from this output?
which type of attack does the attacker attempt to overload the CAM table on a switch so that the switch acts a
In which type of attack does the attacker attempt to overload the CAM table on a switch so that the switch acts as a hub?
What is the problem when 237 dials 972551915?
Which two actions does Cisco recommend to solve this issue?
A customer is integrating two video solutions between regions using a Cisco Unified Border Element and
finds that some of the RTP payloads are not compatible with the Cisco Unified
Border Element configuration. Which two actions does Cisco recommend to solve this issue? (Choose
two.)
Which syslog severity level is level number 7?
Which syslog severity level is level number 7?