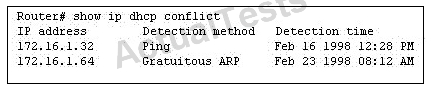
Which rule does the DHCP server use when there is an IP address conflict?
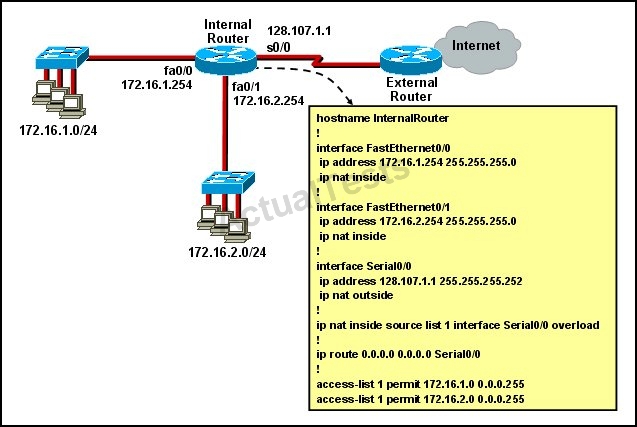
What statement is true of the configuration for this network?
Which two tasks does the Dynamic Host Configuration Protocol perform?
Which two tasks does the Dynamic Host Configuration Protocol perform? (Choose two.)
which two IP addresses should never be assignable to hosts?
When a DHCP server is configured, which two IP addresses should never be assignable to hosts?
(Choose two.)
Which two statements about static NAT translations are true?
Which two statements about static NAT translations are true? (Choose two.)
Which two statements are true?
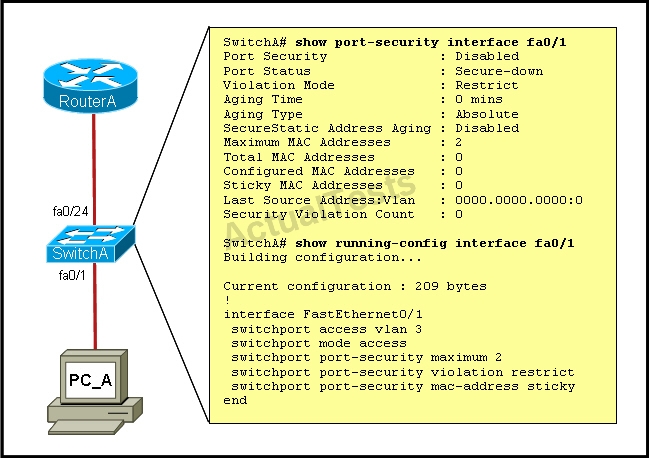
A network administrator needs to configure port security on a switch. Which two statements are
true? (Choose two.)
Which two of these changes are necessary for SwitchA to meet the requirements?
A junior network administrator was given the task of configuring port security on SwitchA to allow
only PC_A to access the switched network through port fa0/1. If any other device is detected, the
port is to drop frames from this device. The administrator configured the interface and tested it with
successful pings from PC_A to RouterA, and then observes the output from these two show
commands.
Which two of these changes are necessary for SwitchA to meet the requirements? (Choose two.)
Which set of commands is recommended to prevent the use of a hub in the access layer?
Which set of commands is recommended to prevent the use of a hub in the access layer?
How does using the service password-encryption command on a router provide additional security?
How does using the service password-encryption command on a router provide additional
security?
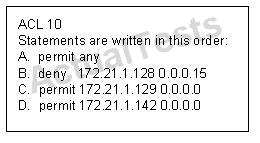
How can the ACL statements be re-arranged so that the system works as intended?
Statements A, B, C, and D of ACL 10 have been entered in the shown order and applied to
interface E0 inbound, to prevent all hosts (except those whose addresses are the first and last IP
of subnet 172.21.1.128/28) from accessing the network. But as is, the ACL does not restrict
anyone from the network. How can the ACL statements be re-arranged so that the system works
as intended?