what would be the resulting dynamically configured ACL for the return traffic on the outside ACL?
How many messages does Internet Key Exchange use to negotiate SA characteristic when it runs in aggressive mod
How many messages does Internet Key Exchange use to negotiate SA characteristic when it runs
in aggressive mode?
Which option is the resulting action in a zone-based policy firewall configuration with these conditions? Sour
Which option is the resulting action in a zone-based policy firewall configuration with these conditions?
Source: Zone 1
Destination: Zone 2
Zone pair exists?: Yes
Policy exists?: No
What are the default values for GRE tunnel keeplive time and number of retries?
What are the default values for GRE tunnel keeplive time and number of retries?
which five types of traffic are permitted?
A Cisco ASA appliance has three interfaces configured. The first interface is the inside interface with a security
level of 100. The second interface is the DMZ interface with a security level of 50. The third interface is the
outside interface with a security level of 0. By default, without any access list configured, which five types of
traffic are permitted? (Choose five.)
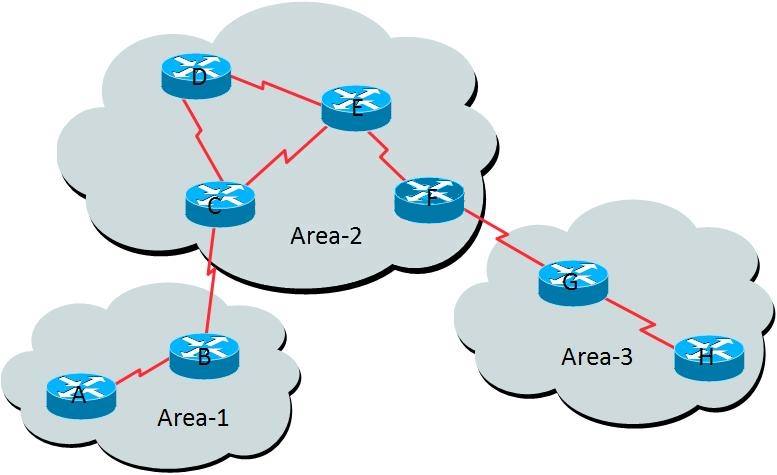
Which routers must be Level 2 routers?
Which two protocols enable Cisco Configuration Professional to pull IPS alerts from a Cisco ISR router?
Which two protocols enable Cisco Configuration Professional to pull IPS alerts from a Cisco ISR router?
(Choose two.)
which device does the first router that connects with the multicast source send the register message?
In PIM-SM operations, to which device does the first router that connects with the multicast source
send the register message?
Which two functions are required for IPsec operation?
Which two functions are required for IPsec operation? (Choose two.)