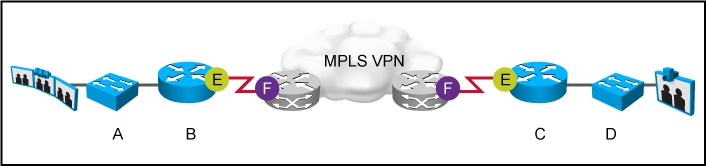
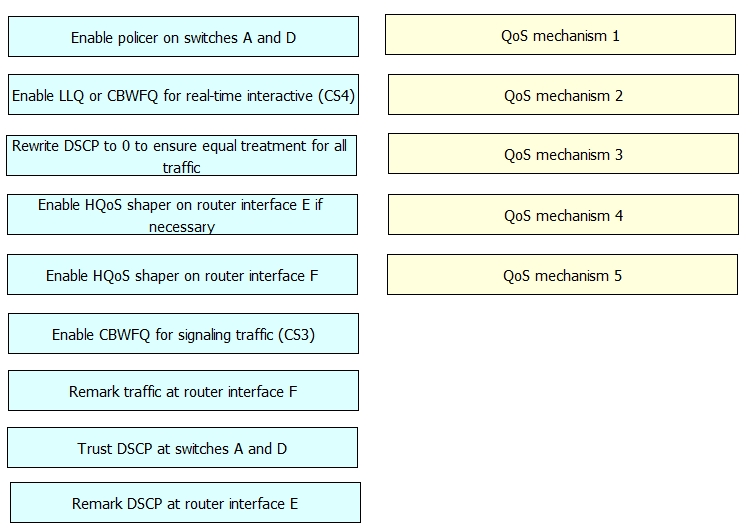
rag and drop the necessary QoS mechanisms from the left to the right in any order.
Which three techniques can be used to provide IPv6 firs…
Which three techniques can be used to provide IPv6 first-hop security to prevent man-in-themiddle attacks? (Choose three.)
Which two mechanisms can be used independently to impro…
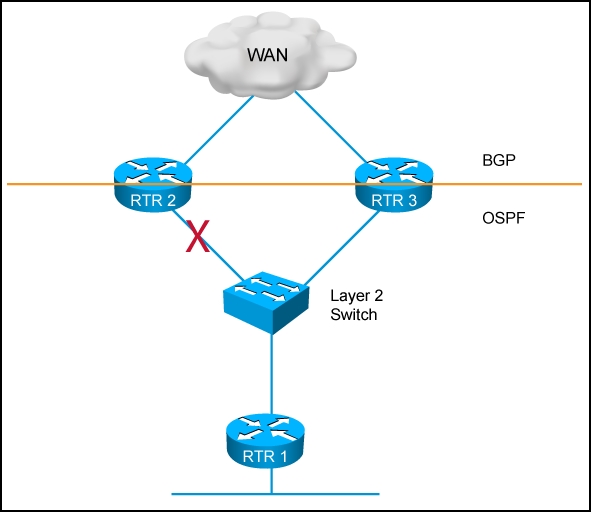
Refer to the exhibit.
RTR 1 uses RTR 2 as the primary WAN exit point. When a failure occurs in the link connected to
RTR 2 LAN, it takes about 40 seconds for RTR 1 to use the backup path via RTR 3. Which two
mechanisms can be used independently to improve the failure detection time to 1 second or
less when RTR 1 failover to RTR3? (Choose two.)
Which network topology is characterized by a link fate-…
Which network topology is characterized by a link fate-sharing situation?
Which design change should be made to prevent this pack…
Refer to the exhibit.
This network is running IS-IS as the single routing protocol and the LSP and SPF timers are
aggressively configured so the network converges in subsecond. The customer reports that
router B had a memory crash and reloaded, which resulted in some packets from the
application being lost. The application servers are behind router G and the end users are behind
router H. Which design change should be made to prevent this packet-loss problem from
reoccurring?
Which feature should you implement to eliminate the ris…
Refer to the exhibit.You are designing MPLS-TE for this network. The links from Perth to Sydney and from Perth to
Adelaide share the same optical fiber in one given segment. Which feature should you
implement to eliminate the risk that a backup tunnel is installed over the same optical fiber as
the primary one?
Which two benefits does using virtual PortChannel techn…
Which two benefits does using virtual PortChannel technology provide? (Choose two).
Which three actions can you take to allow this visibility?
You must measure the amount of traffic that a mobile packet gateway produces when mobile
phones access the service provider’s internal applications, rather than the Internet. Backbone
queuing can be properly designed as a result of this analysis. This traffic is in the multiple
Gigabits per second order of magnitude. Which three actions can you take to allow this
visibility? (Choose three.)
Which three other tools or techniques should be employe…
You are a network designer who must fine tune the convergence of an IS-IS network. The failure
detection mechanism has been addressed with reliable loss-of-signal at the interface level.
Which three other tools or techniques should be employed to achieve your requirements?
(Choose three.)
Which two features should you enable as part of this design?
To improve the stability of the network and protect it from intrusions, you must design control
plane security. Which two features should you enable as part of this design? (Choose two.)