which configuration task is needed to enable that port to function as a routed port?
When configuring a routed port on a Cisco multilayer switch, which configuration task is needed to
enable that port to function as a routed port?
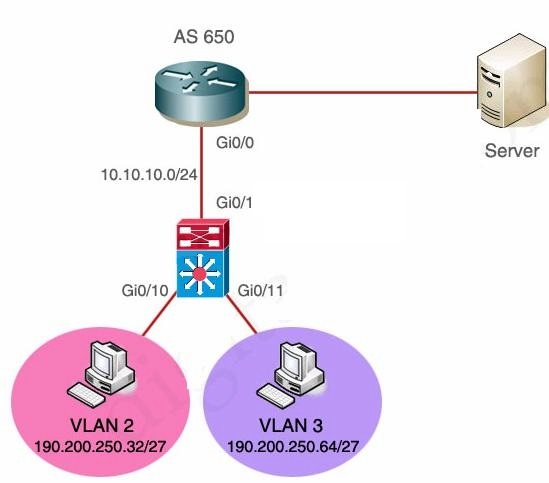
Configure the Multilayer Switch so that PCs from VLAN 2 and VLAN 3 can communicate with the Server.
What is the most likely cause of the problem?
A standalone wireless AP solution is being installed into the campus infrastructure. The access
points appear to boot correctly, but wireless clients are not obtaining correct access. You verify
that this is the local switch configuration connected to the access point:
interface ethernet 0/1
switchport access vlan 10
switchport mode access
spanning-tree portfast
mls qos trust dscp
What is the most likely cause of the problem?
which two required items are configured at an access layer switch that will be connected to an IP phone to pro
During the implementation of a voice solution, which two required items are configured at an
access layer switch that will be connected to an IP phone to provide VoIP communication?
(Choose two.)
Which two statements best describe Cisco IOS IP SLA?
Which two statements best describe Cisco IOS IP SLA? (Choose two.)
Which two items best describe a Cisco IOS IP SLA responder?
Which two items best describe a Cisco IOS IP SLA responder? (Choose two.)
What does the interface subcommand switchport voice vlan 222 indicate?
What does the interface subcommand switchport voice vlan 222 indicate?
What is the most likely cause of this problem?
A campus infrastructure supports wireless clients via Cisco Aironet AG Series 1230, 1240, and
1250 access points. With DNS and DHCP configured, the 1230 and 1240 access points appear to
boot and operate normally. However, the 1250 access points do not seem to operate correctly.
What is the most likely cause of this problem?
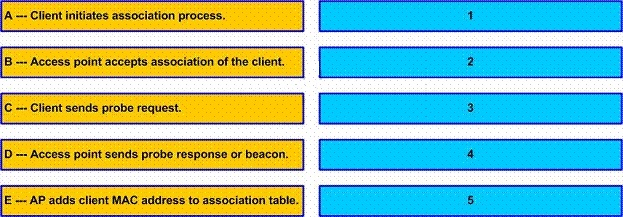
Drag the items to the proper locations.
where are the two optimal locations for trust boundaries to be configured by the network administrator?
A network is deployed using recommended practices of the enterprise campus network model,
including users with desktop computers connected via IP phones. Given that all components are
QoS-capable, where are the two optimal locations for trust boundaries to be configured by the
network administrator? (Choose two.)