What does the command udld reset accomplish?
What does the command udld reset accomplish?
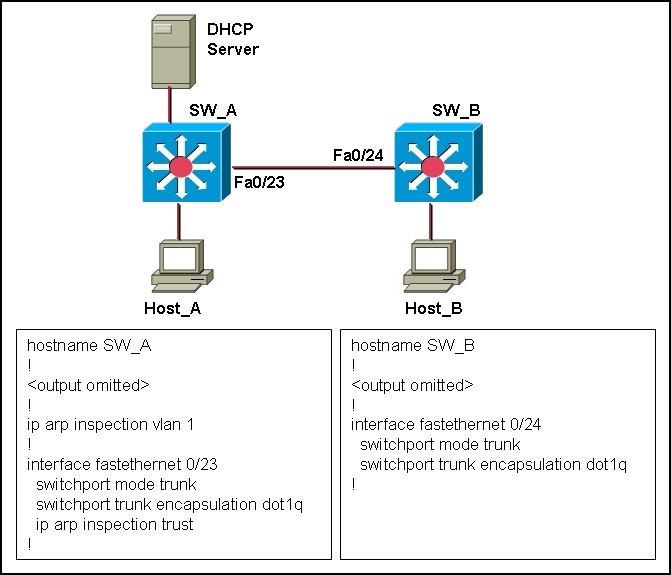
What would the outcome be if Host_B initiated an ARP spoof attack toward Host_A?
Which statement is true about Layer 2 security threats?
Which statement is true about Layer 2 security threats?
What is the purpose of this global configuration command made on R1?
On a Company switch named R1 you configure the following:
ip arp inspection vlan 10-12, 15
What is the purpose of this global configuration command made on R1?
Which two of the following statements are true?
What are two methods of mitigating MAC address flooding attacks?
What are two methods of mitigating MAC address flooding attacks? (Choose two.)
What is one method that can be used to prevent VLAN hopping?
What is one method that can be used to prevent VLAN hopping?
Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering the spanning-tree top
Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering the
spanning-tree topology of a network?
What two steps can be taken to help prevent VLAN hopping?
What two steps can be taken to help prevent VLAN hopping? (Choose two.)
how is the attacker able to gather information?
When an attacker is using switch spoofing to perform VLAN hopping, how is the attacker able to
gather information?