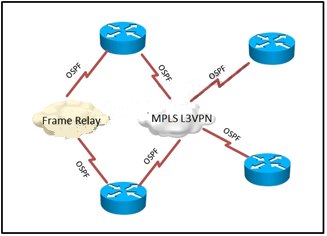
Which feature could be used in the ?MPLS VPN service provider network to support the design requirement by ens
An enterprise is migrating its single-area OSPF network from a Frame Relay WAN service to an
MPLS L3VPN service. Frame Relay will remain in only a few sites that require increased resiliency
via two different WAN connections.
Which feature could be used in the ?MPLS VPN service provider network to support the design
requirement by ensuring that during normal operation, intersite traffic will only use the MPLS VPN
service and not the old Frame Relay service?
How will a router function if the QoS mechanism of congestion avoidance is integrated into the existing networ
You have been hired to redesign a network due to issues with congestion. How will a router
function if the QoS mechanism of congestion avoidance is integrated into the existing network
design?
which two ways is IPv4 and IPv6 traffic handled in a network design that uses QoS deployment options?
In which two ways is IPv4 and IPv6 traffic handled in a network design that uses QoS deployment
options? (Choose two.)
How would you design your solution to map the DSCP value properly so that the traffic is assigned to the resp
You are the lead network designer hired by Service Provider XYZ to deploy CoS functionality on
the core MPLS network (P routers). The goal of the network design is to provide a complete CoS
solution to all customers that purchase services such as dedicated internet access, MPLS L3VPN,
and L2VPN (pseudowire). Service Provider XYZ has these design requirements:
The network supports four service queues with equal treatment for delay, jitter, and packet loss.
Queues are numbered 0-3, where 0 is the default queue.
Three queues have one treatment.
One queue has either one or two treatments.
How would you design your solution to map the DSCP value properly so that the traffic is assigned
to the respective queues in the Service Provider XYZ MPLS core network?
Which two threshold-crossing metrics should you include in this report?
As part of a new network design, you are helping the Network Management Team to develop a
proactive report to identify places in the network where problems may happen. The network
management tool can poll the network devices only via SNMP GET operations. Which two
threshold-crossing metrics should you include in this report? (Choose two.)
What three key performance indicators would you use to track media quality?
You are identifying performance management requirements for a VoIP migration. What three key
performance indicators would you use to track media quality? (Choose three.)
What is your design recommendation?
Your enterprise customer has asked where they should deploy flow monitoring in their network to
monitor traffic between branch offices. What is your design recommendation?
Which technology would you recommend to enhance security by limiting traffic that could originate from a hacke
You are a network designer and have been asked to consult with your server operations team to
further enhance the security of the network. The operations team provides you with these details
about the network:
A pool of servers is accessed by numerous data centers and remote sites.
The servers are accessed via a cluster of firewalls.
The firewalls are configured properly and are not dropping traffic.
The firewalls occasionally cause asymmetric routing of traffic within the server data center.
Which technology would you recommend to enhance security by limiting traffic that could originate
from a hacker compromising a workstation and redirecting flows at the servers?
which switch security option should you investigate to ensure that authorized ARP responses take place accordi
You have been hired by Acme Corporation to evaluate their existing network and determine if the
current network design is secure enough to prevent man-in-the-middle attacks. When evaluating
the network, which switch security option should you investigate to ensure that authorized ARP
responses take place according to known IP-to-MAC address mapping?
Which solution meets these requirements?
A company has these requirements for access to their wireless and wired corporate LANs using
802.1x:
Client devices that are corporate assets and have been joined to the Active Directory domain are
allowed access.
Personal devices must not be allowed access.
Clients and access servers must be mutually authenticated.
Which solution meets these requirements?