What are two methods of mitigating MAC address flooding attacks?
What are two methods of mitigating MAC address flooding attacks? (Choose two.)
How does 802.1Q trunking keep track of multiple VLANs?
The Company core switches use 802.1Q trunks to connect to each other. How does 802.1Q
trunking keep track of multiple VLANs?
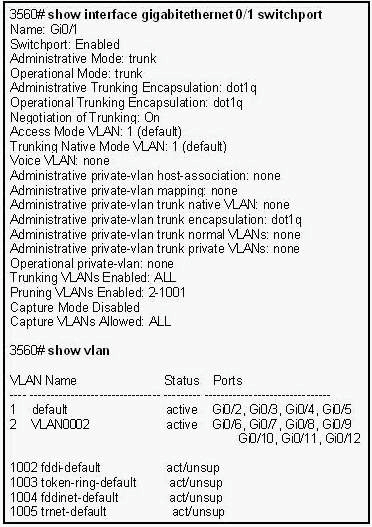
What information can be derived from the output?
which two statements are true?
What is one method that can be used to prevent VLAN hopping?
What is one method that can be used to prevent VLAN hopping?
Which three statements are correct with regard to the IEEE 802.1Q standard?
The core Company switches are configured to use 802.1Q trunks. Which three statements
are correct with regard to the IEEE 802.1Q standard? (Select three)
Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering the spanning-tree top
Why is BPDU guard an effective way to prevent an unauthorized rogue switch from altering
the spanning-tree topology of a network?
Which statement describes Dynamic Trunking Protocol (DTP) desirable mode?
Switch R1 has been configured with DTP using the desirable option. Which statement
describes Dynamic Trunking Protocol (DTP) desirable mode?
What two steps can be taken to help prevent VLAN hopping?
What two steps can be taken to help prevent VLAN hopping? (Choose two.)
Which switch command enables a trunking protocol that appends a four byte CRC to the packet?
You need to configure a new Company switch for trunking. Which switch command enables
a trunking protocol that appends a four byte CRC to the packet?