Which statement about the NAT/PAT configuration is true?
which access rule is applied inbound to the inside inte…
By default, which access rule is applied inbound to the inside interface?
how long is the attacker who is performing the scan shunned?
What else must be enabled in order to make it work?
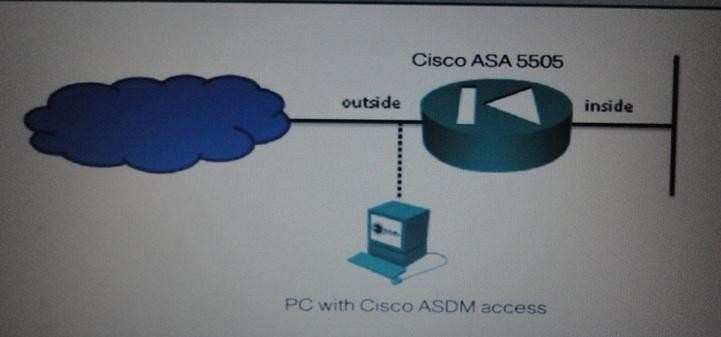
Scenario: To access Cisco ASDM, click the PC icon in the Topology window, ASDM and answer the following question as:
The Cisco ASA administration must enable the Cisco ASA to automatically drop suspicious botnet traffic. After the Cisco ASA administrator entered the initial
configuration, the Cisco ASA is not automatically dropping the suspicious botnet traffic. What else must be enabled in order to make it work?
Which two statements about the running configuration of…
Which statement about the Cisco ASA configuration is true?
Which two statements about why the Cisco ASA configurat…
Refer to the exhibit and to the four HTTP inspection requirements and the Cisco ASA configuration.
Which two statements about why the Cisco ASA configuration is not meeting the specified HTTP inspection requirements are true? (Choose two.)
1. All outside clients can use only the HTTP GET method on the protected 10.10.10.10 web server.
2. All outside clients can access only HTTP URIs starting with the “/myapp” string on the protected 10.10.10.10 web server.
3. The security appliance should drop all requests that contain basic SQL injection attempts (the string “SELECT” followed by the string “FROM”) inside HTTP
arguments.
4. The security appliance should drop all requests that do not conform to the HTTP protocol.
Which two configurations are the minimum needed to enab…
Which two configurations are the minimum needed to enable EIGRP on the Cisco ASA appliance? (Choose two.)
Which three statements are the default security policy …
Which three statements are the default security policy on a Cisco ASA appliance? (Choose three.)