What should you do?
Which crypto map tag is being used on the Cisco ASA?
Scenario:
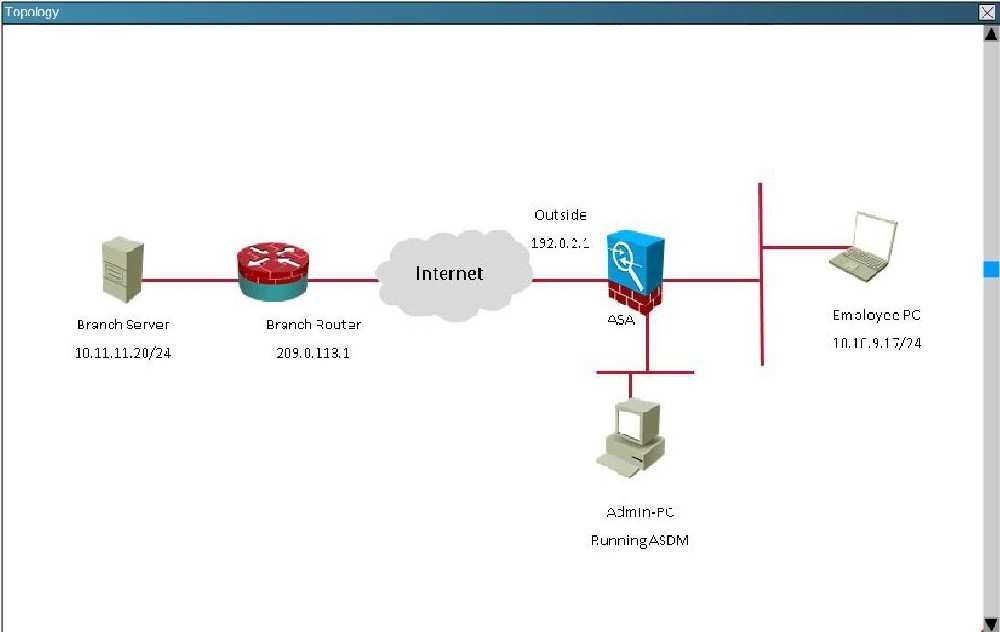
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
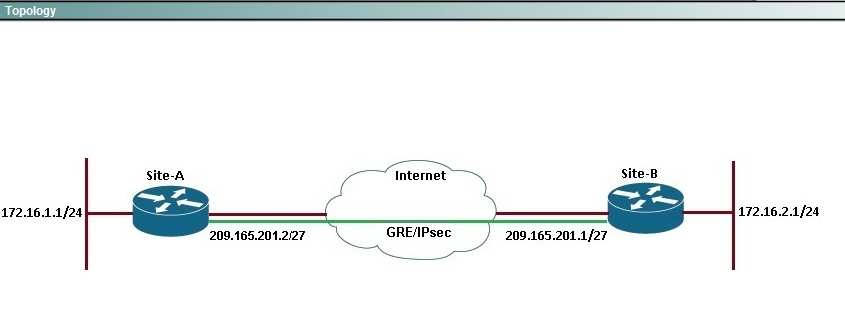
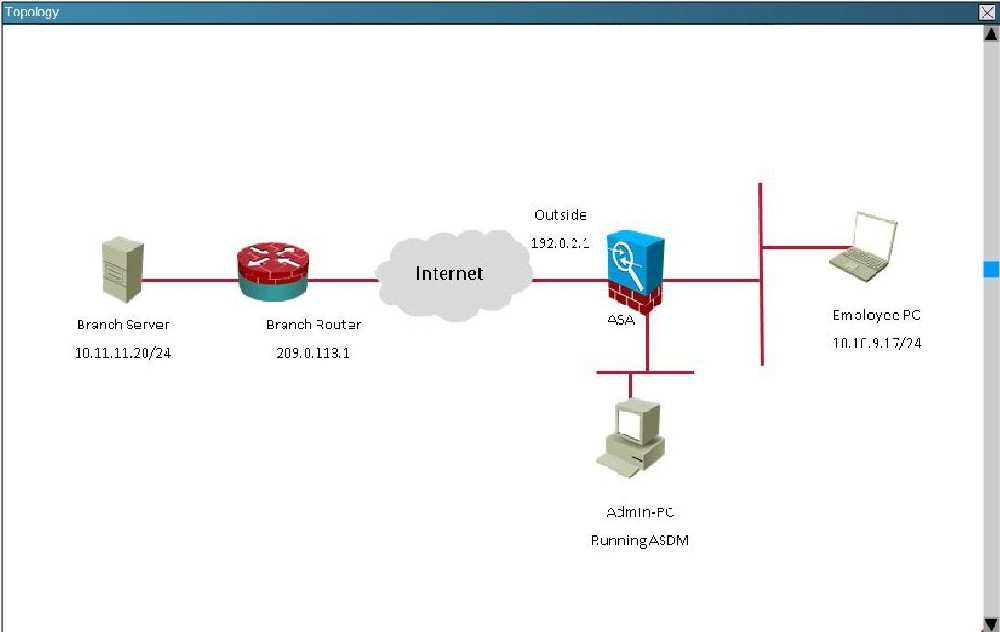
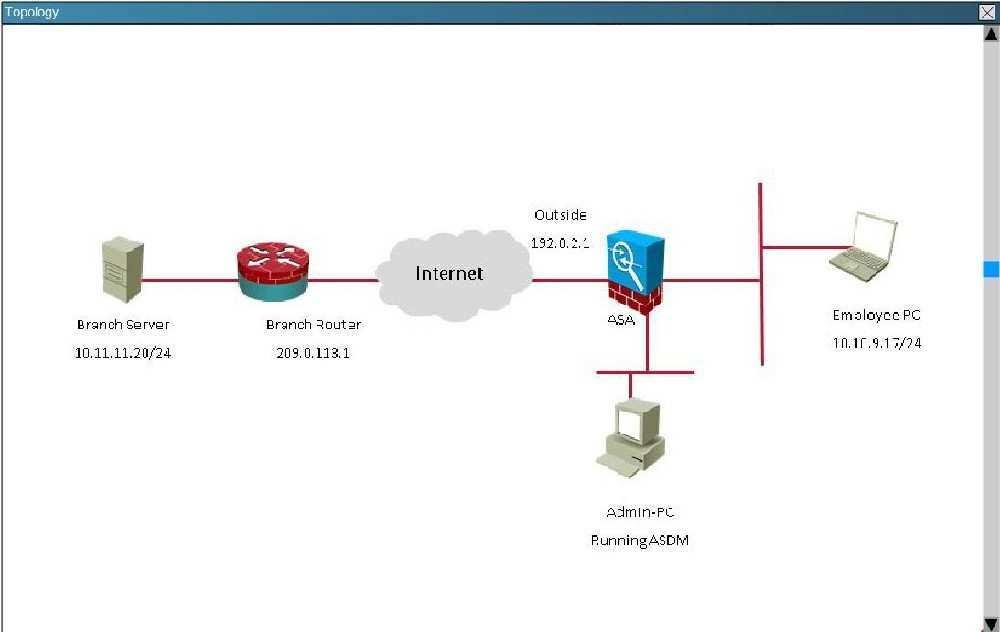
Topology:
Which crypto map tag is being used on the Cisco ASA?
what state is the IKE security association in on the Ci…
Scenario:
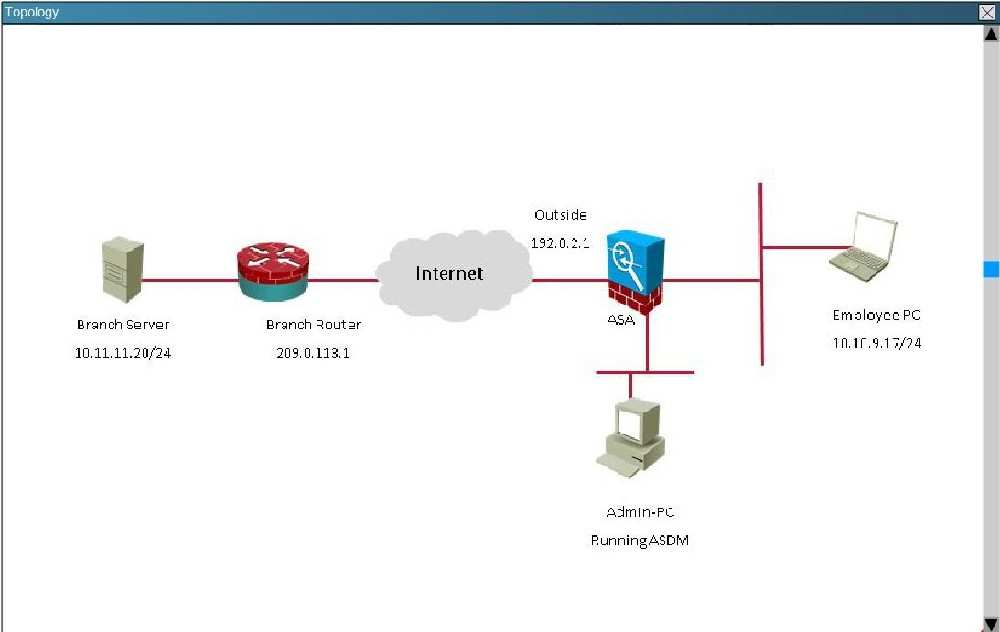
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
In what state is the IKE security association in on the Cisco ASA?
Which transform set is being used on the branch ISR?
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
Which transform set is being used on the branch ISR?
What is being used as the authentication method on the …
Scenario:
You are the senior network security administrator for your organization. Recently and junior engineer configured a site-to-site IPsec VPN connection between your
headquarters Cisco ASA and a remote branch office.
You are now tasked with verifying the IKEvl IPsec installation to ensure it was properly configured according to designated parameters. Using the CLI on both the
Cisco ASA and branch ISR. verify the IPsec configuration is properly configured between the two sites.
NOTE: the show running-config command cannot be used for the this exercise.
Topology:
What is being used as the authentication method on the branch ISR?
Which protocol does DTLS use for its transport?
Which protocol does DTLS use for its transport?
Which two technologies are considered to be Suite B cry…
Which two technologies are considered to be Suite B cryptography? (Choose two.)
Which exchange does this debug output represent?
which type of key is the shared secret?
In the Diffie-Hellman protocol, which type of key is the shared secret?
Which technology must be installed on the client comput…
Which technology must be installed on the client computer to enable users to launch applications from a Clientless SSL VPN?