You have been tasked with implementing the above access control as a pre-condition to installing the servers.
CORRECT TEXT
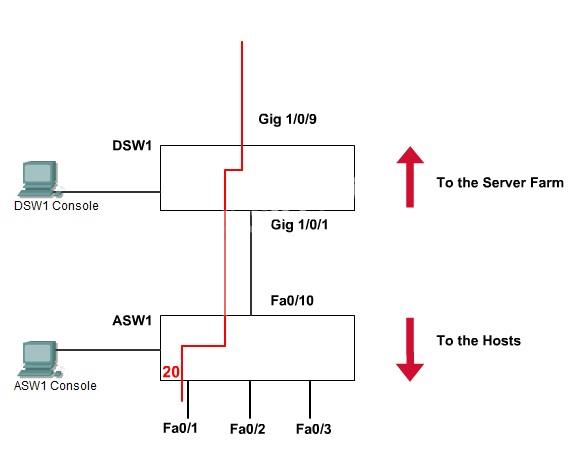
SWITCH.com is an IT company that has an existing enterprise network comprised of two layer 2
only switches; DSW1 and ASW1. The topology diagram indicates their layer 2 mapping. VLAN 20
is a new VLAN that will be used to provide the shipping personnel access to the server. Corporate
polices do not allow layer 3 functionality to be enabled on the switches. For security reasons, it is
necessary to restrict access to VLAN 20 in the following manner:
• Users connecting to VLAN 20 via portfO/1 on ASW1 must be authenticated before they are
given access to the network. Authentication is to be done via a Radius server:
• Radius server host: 172.120.40.46
• Radius key: rad123
• Authentication should be implemented as close to the host as possible.
• Devices on VLAN 20 are restricted to the subnet of 172.120.40.0/24.
• Packets from devices in the subnet of 172.120.40.0/24 should be allowed on VLAN 20.
• Packets from devices in any other address range should be dropped on VLAN 20.
• Filtering should be implemented as close to the serverfarm as possible.
The Radius server and application servers will be installed at a future date. You have been tasked
with implementing the above access control as a pre-condition to installing the servers. You must
use the available IOS switch features.
What is the default HSRP priority?
What is the default HSRP priority?
Which two commands can protect against this problem?
A rogue device has connected to the network and has become the STP root bridge, which has
caused a network availability issue.
Which two commands can protect against this problem? (Choose two.)
what extent will the Cisco IPS sensor contribute data to the Cisco SensorBase network?
Which option is a benefit of using VSS?
Which option is a benefit of using VSS?
which two interface configuration commands help prevent VLAN hopping attacks?
According to Cisco best practices, which two interface configuration commands help prevent
VLAN hopping attacks? (Choose two.)
Which First Hop Redundancy Protocol is an IEEE Standard?
Which First Hop Redundancy Protocol is an IEEE Standard?
Which two statements about Signature 1104 are true?
What is the default amount by which the hot standby priority for the router is decremented or incremented when
What is the default amount by which the hot standby priority for the router is decremented or
incremented when the interface goes down or comes back up?
which two types of Layer 2 attacks?
When it is configured in accordance to Cisco best practices, the switchport port-security maximum
command can mitigate which two types of Layer 2 attacks? (Choose two.)