which interface on a Cisco ASA 1000V firewall should a security profile be applied when a VM sits behind it?
To which interface on a Cisco ASA 1000V firewall should a security profile be applied when a VM
sits behind it?
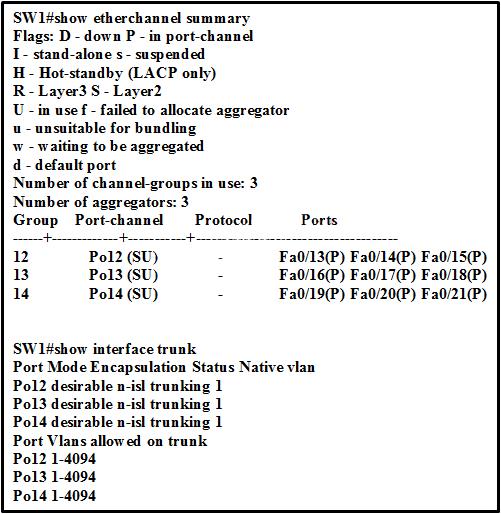
Which EtherChannel negotiation protocol is configured on the interface f0/13 – f0/15?
Which action can the engineer take to resolve this issue?
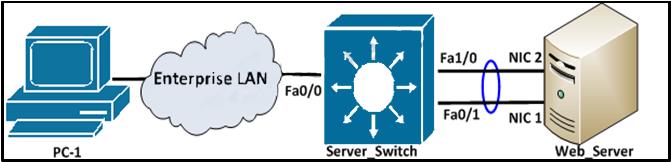
Refer to the exhibit.
Users of PC-1 experience slow connection when a webpage is requested from the server. To
increase bandwidth, the network engineer configured an EtherChannel on interfaces Fa1/0 and
Fa0/1 of the server farm switch, as shown here:
Server_Switch#sh etherchannel load-balance
EtherChannel Load-Balancing Operational State (src-mac):
Non-IP: Source MAC address
IPv4: Source MAC address
IPv6: Source IP address
Server_Switch#
However, traffic is still slow. Which action can the engineer take to resolve this issue?
Which feature must you configure to open data-channel pinholes for voice packets that are sourced from a TRP w
You are configuring a Cisco IOS Firewall on a WAN router that is operating as a Trusted Relay
Point (TRP) in a voice network. Which feature must you configure to open data-channel pinholes
for voice packets that are sourced from a TRP within the WAN?
Which Cisco monitoring solution displays information and important statistics for the security devices in a ne
Which Cisco monitoring solution displays information and important statistics for the security
devices in a network?
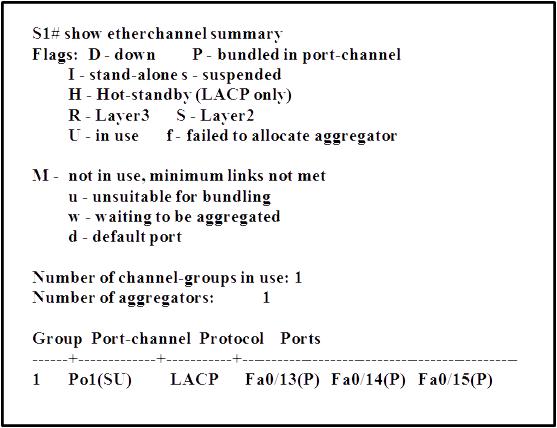
what happens to all ports in the bundle?
A network engineer changed the port speed and duplex setting of an existing EtherChannel
bundle that uses the PAgP protocol. Which statement describes what happens to all ports in the
bundle?
Which two voice protocols can the Cisco ASA inspect?
Which two voice protocols can the Cisco ASA inspect? (Choose two.)
Which statement about using EtherChannel on Cisco IOS switches is true?
Which statement about using EtherChannel on Cisco IOS switches is true?
Which three search parameters are supported by the Email Security Monitor?
Which three search parameters are supported by the Email Security Monitor? (Choose three.)