Which Cisco IOS command is used to verify that either the Cisco IOS image, the configuration files, or both ha
Which Cisco IOS command is used to verify that either the Cisco IOS image, the configuration
files, or both have been properly backed up and secured?
Which key method is used to detect and prevent attacks by use of IDS and/or IPS technologies?
Which key method is used to detect and prevent attacks by use of IDS and/or IPS technologies?
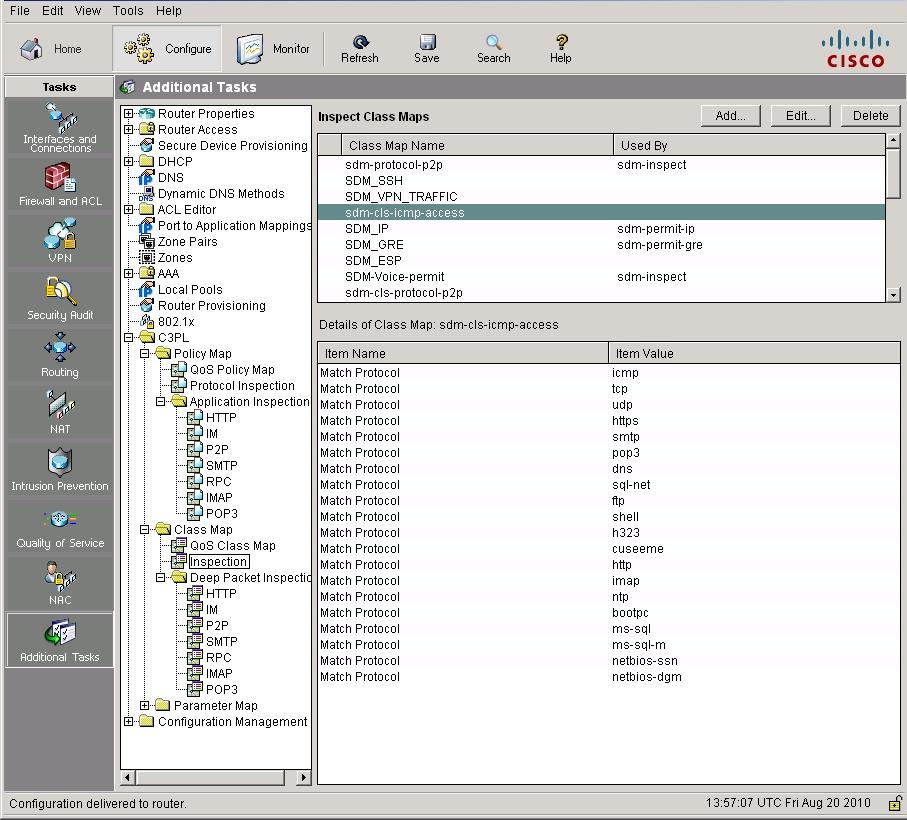
Which statements is correct regarding the "sdm-permit" policy map?
Instructions
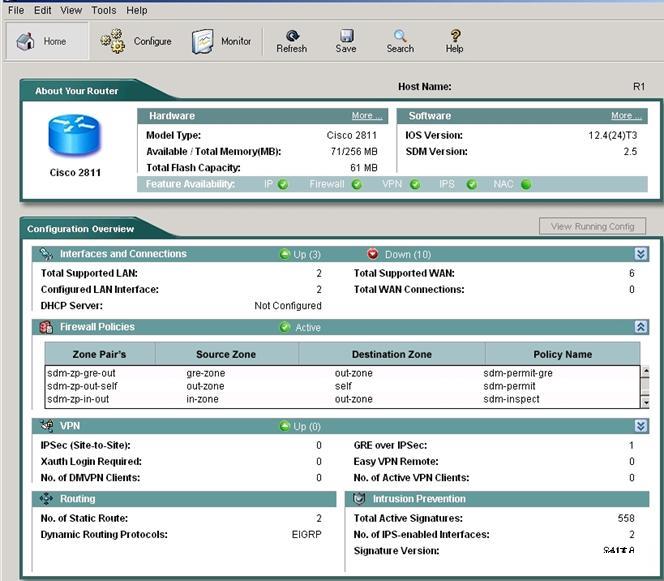
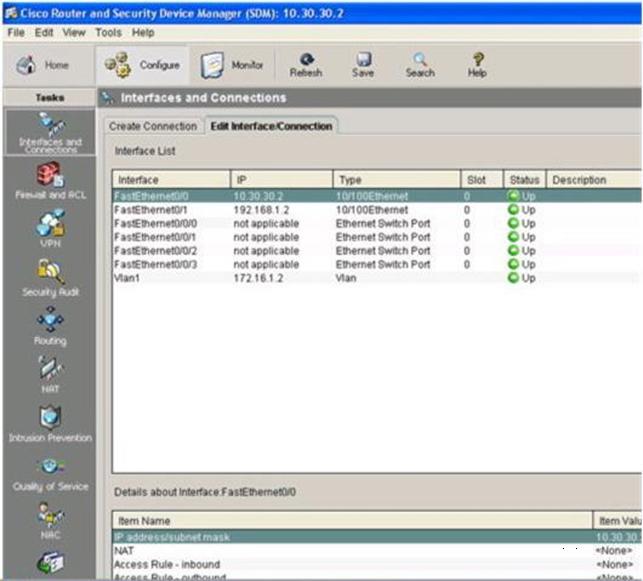
To access the Cisco Router and Security Device Manager(SDM) utility click on the console host
icon that is connected to a ISR router.
You can click on the grey buttons below to view the different windows.
Each of the windows can be minimized by clicking on the [-].You can also reposition a window by
dragging it by the title bar.
The “Tab” key and most commands that use the “Control”or “Escape” keys are not supported and
are not necessary to complete this simulation.
Which statements is correct regarding the “sdm-permit” policy map?
Which item was cleared during the reset?
An AP was reset while working on the correct association to a Cisco WCS version 7.0.
Which item was cleared during the reset?
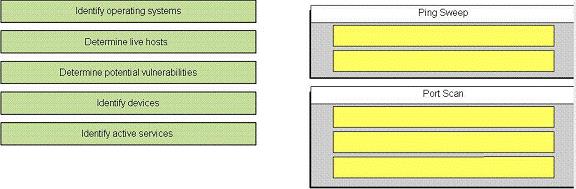
What are two characteristics of the SDM Security Audit wizard?
What are two characteristics of the SDM Security Audit wizard? (Choose two.)