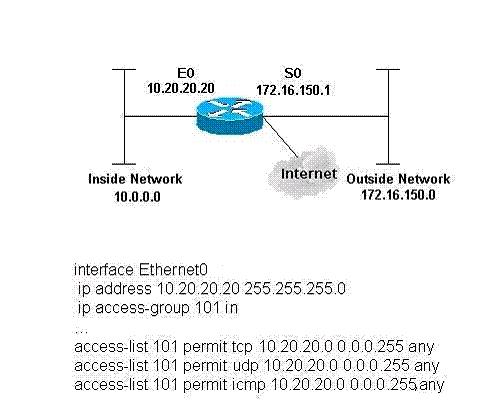
Which statement is true?
place the correct descriptions in the proper locations.
Which three rules are valid transfer rules in Cisco Unity Connection?
Which three rules are valid transfer rules in Cisco Unity Connection? (Choose Three)
Which of the following vulnerabilities may occur while the client and the AP exchange the challenge text over
John works as a network administrator for Web Perfect Inc. The company has a wireless LAN
network. John has configured shared key authentication on a client. The client and the AP start
exchanging the frames to enable authentication. Which of the following vulnerabilities may occur
while the client and the AP exchange the challenge text over the wireless link?
Which Cisco Unity Connection report provides a summary view of the current size, last error condition, and sta
Which Cisco Unity Connection report provides a summary view of the current size, last error
condition, and status of the mailbox store?
how many failed attempts at signing into Cisco Unity Connection is a user allowed before their account is lock
By default, how many failed attempts at signing into Cisco Unity Connection is a user allowed
before their account is locked out?
which service should you activate in Cisco Unity Connection?
To monitor the service health and performance, which service should you activate in Cisco Unity
Connection?
Which of these can be used to authenticate the IPsec peers during IKE Phase 1?
Which of these can be used to authenticate the IPsec peers during IKE Phase 1?
What is the most likely cause of this issue?
An administrator is attempting to add a new user in Cisco Unified Communications Manager
Administration but does not see the option to add a new user. What is the most likely cause of this
issue?
Which method is the best method to accomplish this task?
An administrator wants to locate and remove all unassigned directory numbers on the Cisco
Unified Communications Manager system. Which method is the best method to accomplish this
task?