Which statement about the impact of configuring a single SSID to support TKIP and AES encryption simultaneousl
Which statement about the impact of configuring a single SSID to support TKIP and AES
encryption simultaneously is true?
What is the reason behind this problem?
You work as a Network Administrator for Tech Perfect Inc. You have to implement a wireless LAN
network for the company. After implementing the network, you check all the functions and find that
most of its clients try to send data on the same channel at the same time. As a result, a collision
occurs in the network and it affects the communication. What is the reason behind this problem?
which two functions is the pre-shared key used?
When the pre-shared key authentication method is used for WPA or WPA2, for which two
functions is the pre-shared key used? (Choose two.)
Which command has he run on the access point?
The network administrator of a company makes some changes in monitor mode of the access
point using a CLI session. This change affects the value of the channels that are monitored in the
monitor mode. Which command has he run on the access point?
Which access list will permit HTTP traffic sourced from host 10.1.129.100 port 3030 destined to host 192.168.1
Which access list will permit HTTP traffic sourced from host 10.1.129.100 port 3030 destined to
host 192.168.1.10?
Which two fields are required parameters when manually creating users on Cisco Unity Connection with predefine
Which two fields are required parameters when manually creating users on Cisco Unity
Connection with predefined templates? (Choose two.)
what percentage of the keyspace must an attacker generally search through until he or she finds the key that d
In a brute-force attack, what percentage of the keyspace must an attacker generally search
through until he or she finds the key that decrypts the data?
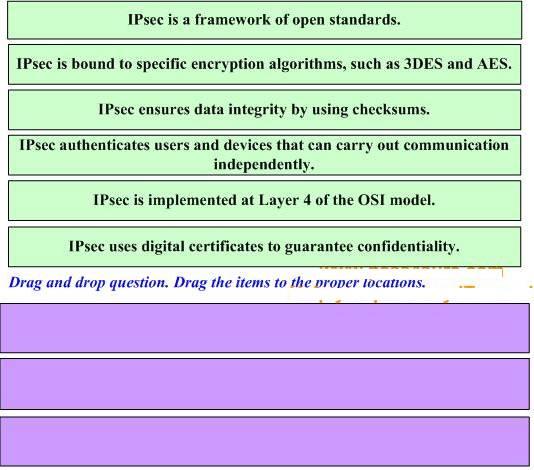
Drag three proper statements about the IPsec protocol on the above to the list on the below.
Which physical layer function can a network administrator perform to determine whether or not any device is
A company has a wireless network. In this network, collisions occur when more than one device
sends data at the same time. Which physical layer function can a network administrator perform to
determine whether or not any device is sending data to the channel?
Where can this behavior be changed?
Users report that all external callers are leaving urgent voice-mail messages. Where can this
behavior be changed?