Which two statements about beacon frames used by access points are true?
Which two statements about beacon frames used by access points are true? (Choose two.)
Which two IPsec protocols are used to protect data in motion?
Which two IPsec protocols are used to protect data in motion? (Choose two.)
Which command indicates the amount of memory (NVRAM, RAM, and flash) in a Cisco device?
Which command indicates the amount of memory (NVRAM, RAM, and flash) in a Cisco device?
which protocol number does Encapsulating Security Payload operate?
On which protocol number does Encapsulating Security Payload operate?
which protocol number does the authentication header operate?
On which protocol number does the authentication header operate?
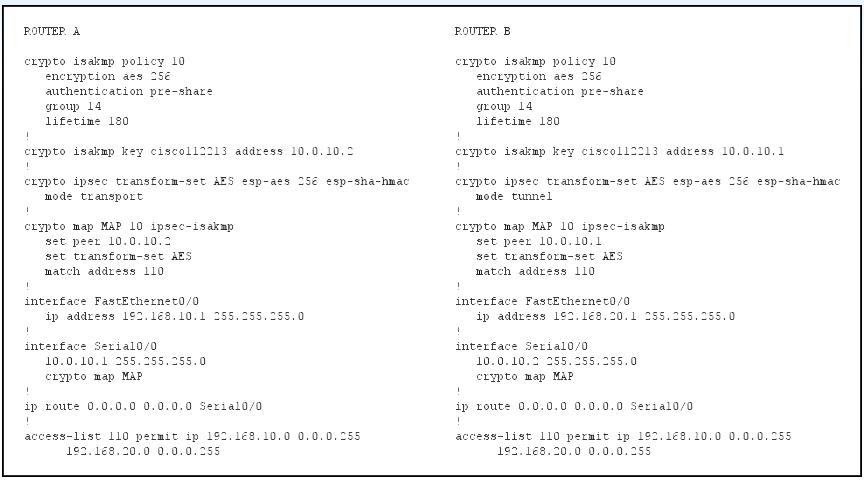
Which two changes must you make to the given IOS site-to-site VPN configuration to enable the routers to form
Which two of the following are true?
Which two of the following are true? (Choose two)
what determination does the access list make about VPN traffic?
In an IPsec VPN, what determination does the access list make about VPN traffic?
what must you do first?
If you have the Cisco ADU installed but want to use the Windows Zero Config utility to configure a
wireless network profile, what must you do first?
Which command verifies phase 2 of an IPsec VPN on a Cisco router?
Which command verifies phase 2 of an IPsec VPN on a Cisco router?