Which statement describes how the sender of the message is verified when asymmetric encryption is used?
Which statement describes how the sender of the message is verified when asymmetric
encryption is used?
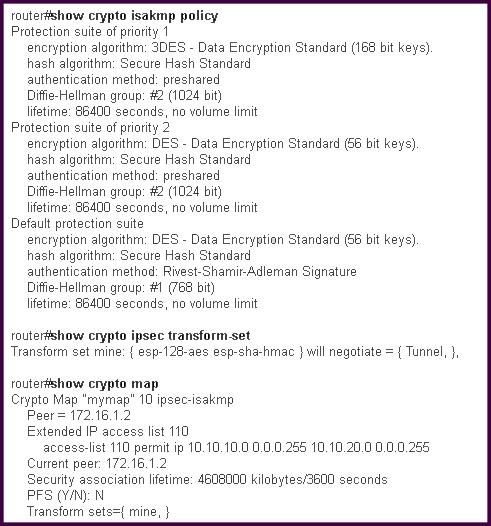
Which three statements about these three show outputs are true?
Which two services are provided by IPsec?
Which two services are provided by IPsec? (Choose two.)
Which three of the following tools should be used to avoid ESD?
ESD is the sudden and momentary electric current that flows between two different objects at
different electrical potentials caused by direct contact or induced by an electrostatic field. Which
three of the following tools should be used to avoid ESD? (Choose three)
Which set of commands assigns a standalone access point an IP address of 10.0.0.24 with a 27- bit subnet mask
Which set of commands assigns a standalone access point an IP address of 10.0.0.24 with a 27-
bit subnet mask and a gateway of 10.0.0.1?
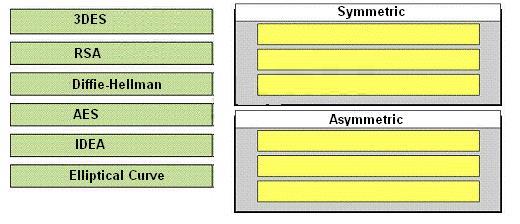
Which two options are symmetric-key algorithms that are recommended by Cisco?
Which two options are symmetric-key algorithms that are recommended by Cisco? (Choose two.)
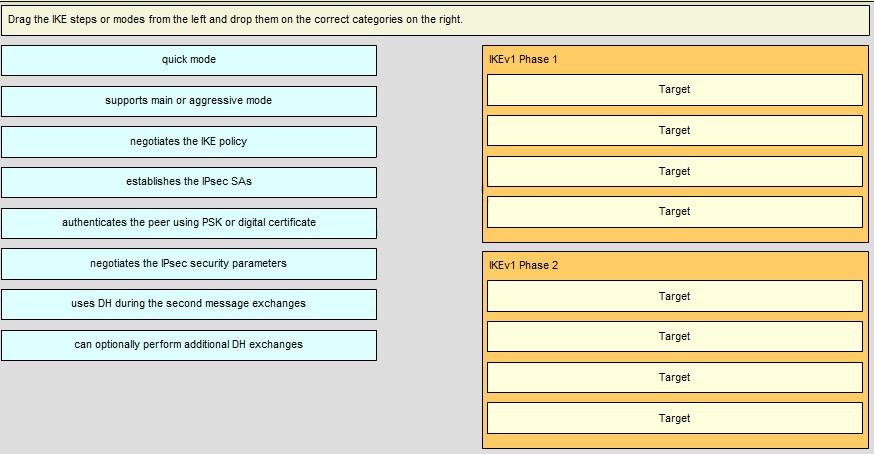
Drag the IKE steps or modes from the left and drop them on the correct categories on the right.
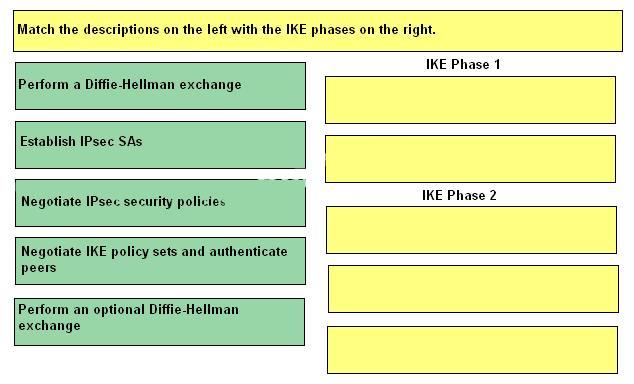
Match the descriptions on the left with the IKE phases on the right.
Drag from Left to Right in Correct Area.
Which technology provides an automated digital certificate management system for use with IPsec?
Which technology provides an automated digital certificate management system for use with
IPsec?