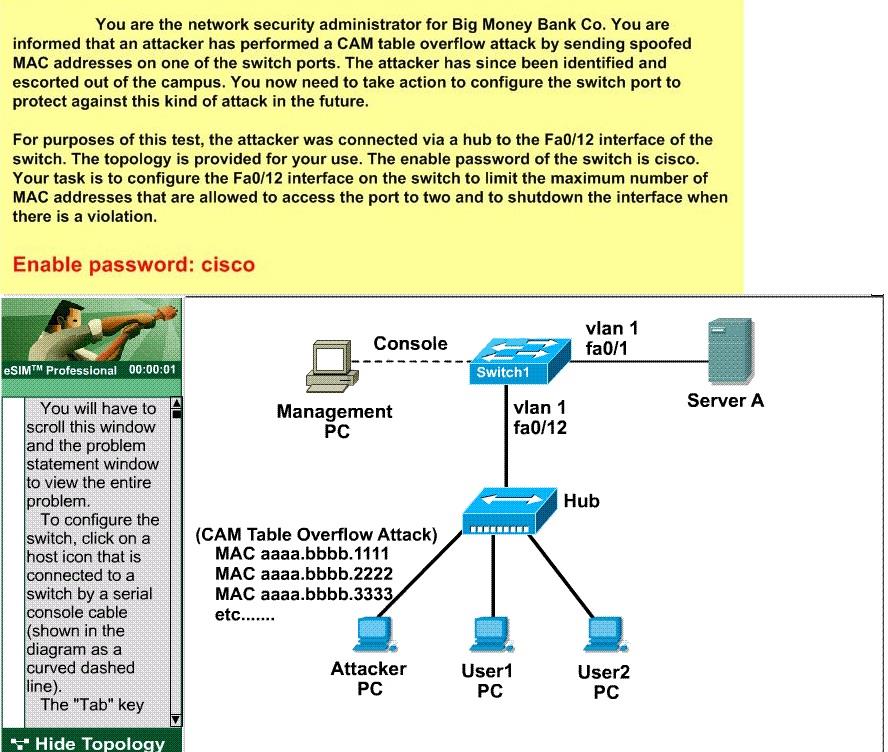
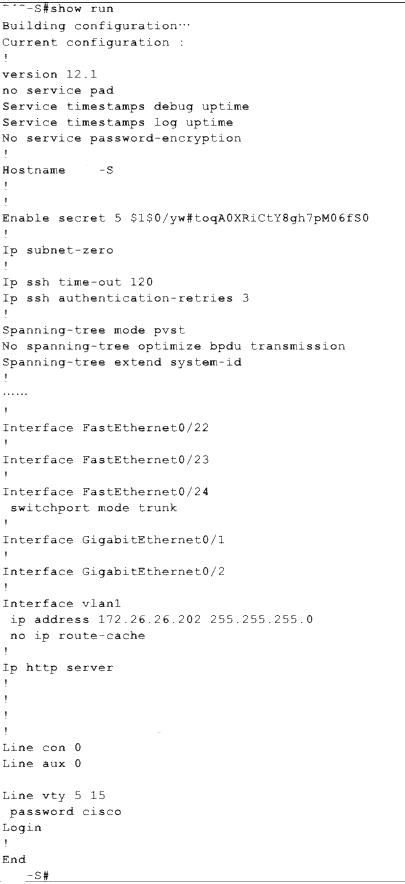
CORRECT TEXT
Drag the port(s) from the left and drop them on the correct STP roles on the right.
Which two countermeasures can mitigate STP root bridge attacks?
Which two countermeasures can mitigate STP root bridge attacks? (Choose two.)
Which type of memory stores the startup configuration file for the Cisco device?
Which type of memory stores the startup configuration file for the Cisco device?
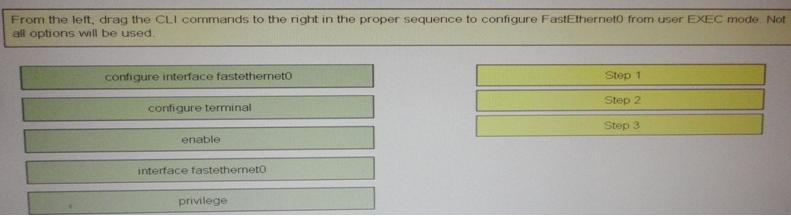
drag the CLI commands to the right in the proper sequence to configure FastEthernet0 from User EXEC mode.
Which two countermeasures can mitigate MAC spoofing attacks?
Which two countermeasures can mitigate MAC spoofing attacks? (Choose two.)
What three authentication methods are generally used in enterprise wireless networks?
What three authentication methods are generally used in enterprise wireless networks? (Choose
three.)
Which statement correctly describes the function of a private VLAN?
Which statement correctly describes the function of a private VLAN?
What are two primary attack methods of VLAN hopping?
What are two primary attack methods of VLAN hopping? (Choose two.)
Which type of attack can be prevented by setting the native VLAN to an unused VLAN?
Which type of attack can be prevented by setting the native VLAN to an unused VLAN?