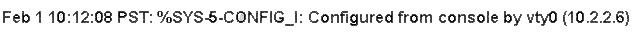Which step is important to take when implementing secure network management?
Which step is important to take when implementing secure network management?
Which four file formats are used when importing a single campus map into the Cisco WCS 5.0?
Which four file formats are used when importing a single campus map into the Cisco WCS 5.0?
(Choose four.)
Which statement is true when you have generated RSA keys on your Cisco router to prepare for secure device man
Which statement is true when you have generated RSA keys on your Cisco router to prepare for
secure device management?
which two statements are true?
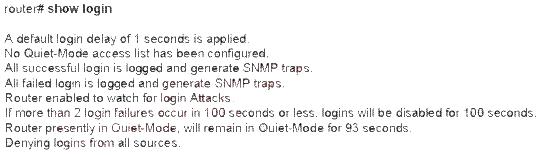
Which statement is correct based on the show login command output shown?
which three operating systems does HyperTerminal not come pre-installed?
On which three operating systems does HyperTerminal not come pre-installed? (Choose three)
Which two considerations about secure network monitoring are important?
Which two considerations about secure network monitoring are important? (Choose two.)
Which two methods will help to mitigate this type of activity?
You suspect that an attacker in your network has configured a rogue Layer 2 device to intercept
traffic from multiple VLANs, which allows the attacker to capture potentially sensitive data.
Which two methods will help to mitigate this type of activity? (Choose two.)
Which two conclusions can be interpreted from these frames?
The network administrator receives complaints of slow wireless network performance and
performs a sniffer trace of the wireless network in preparation for migration to 802.11n. The
sample capture shows frames that contains AP beacons with NonERP_Present bit set to 1 and
frames with RTS/CTS.
Which two conclusions can be interpreted from these frames? (Choose two.)
Which statement describes a best practice when configuring trunking on a switch port?
Which statement describes a best practice when configuring trunking on a switch port?