Which two options represent a threat to the physical installation of an enterprise network?
Which two options represent a threat to the physical installation of an enterprise network? (Choose
two.)
Which two statements about WiMAX technology are true?
Which two statements about WiMAX technology are true? (Choose two.)
Which option represents a step that should be taken when a security policy is developed?
Which option represents a step that should be taken when a security policy is developed?
Which two sets are looped on an RJ-45 T1 loopback plug?
The pins and RJ-45 are numbered from 1 through 8. With the material points of the plug facing
toward you, pin 1 is the leftmost pin. Which two sets are looped on an RJ-45 T1 loopback plug?
(Choose two)
Which type of security control is defense in depth?
Which type of security control is defense in depth?
Which four methods are used by hackers?
Which four methods are used by hackers? (Choose four.)
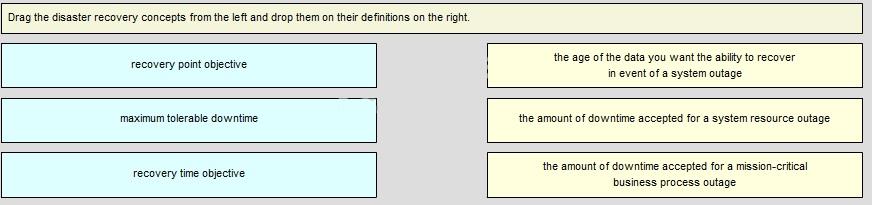
Drag the disaster recovery concepts from the left and drop them on their definitions on the right.
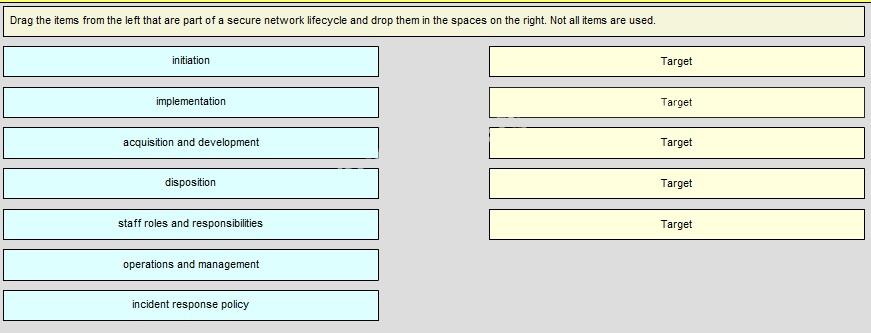
Drag the items from the left that are part of a secure network lifecycle and drop them in the spaces on the ri
Which characteristic is the foundation of Cisco Self-Defending Network technology?
Which characteristic is the foundation of Cisco Self-Defending Network technology?
What are two ways to open Microsoft Notepad on a Windows-based computer?
What are two ways to open Microsoft Notepad on a Windows-based computer? (Choose two)