Which two items are most relevant in documenting RST’s business requirements?
RST Corporation is planning to upgrade its current network. The chief technology officer has
supplied a topology diagram and an IP addressing scheme of the current network during an
interview.
RST has been growing at about twenty percent per year. It has been difficult to maintain customer
support at a satisfactory level. Therefore, the RST board has met with and directed the chief
technology officer to look into network improvements.
Which two items are most relevant in documenting RST’s business requirements? (Choose two.)
hown in the exhibit be configured to allow connectivity between all devices?
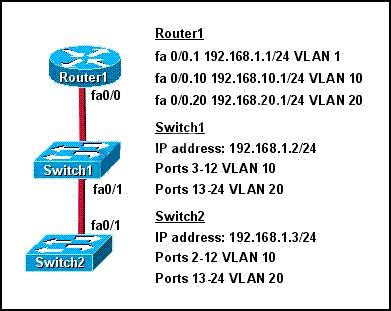
Which two statements are true about interVLAN routing in the topology that is shown in the exhibit?
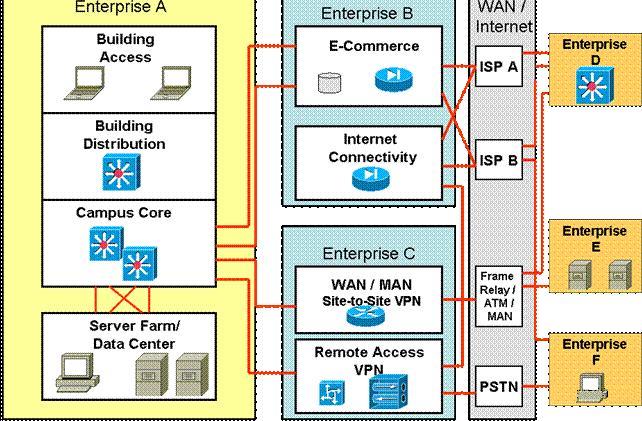
Which module is the Enterprise WAN module?
What is a possible cause of the problem?
A department decides to replace its hub with a Catalyst 2950 switch that is no longer needed by
another department. To prepare the switch for installation, the network administrator has erased
the startup configuration and reloaded the switch. However, PCs that are connected to the switch
experience various connectivity problems. What is a possible cause of the problem?
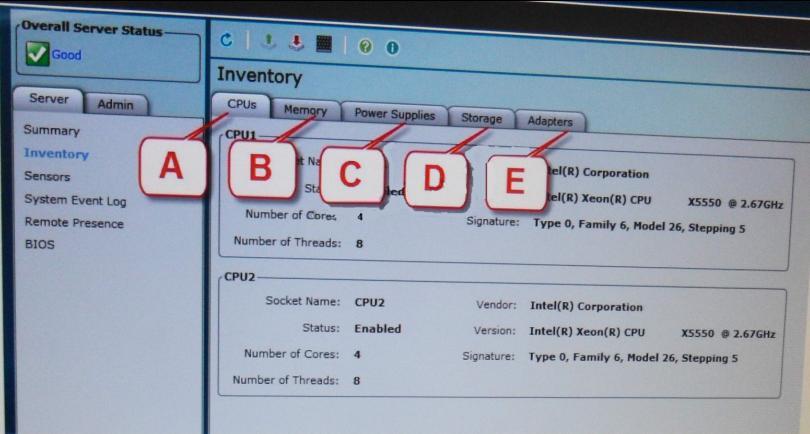
Which tab displays the hard disk drives that are installed?
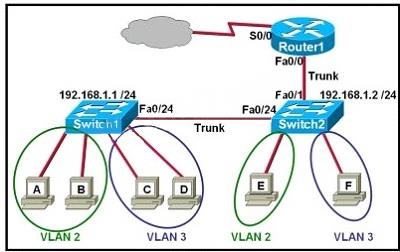
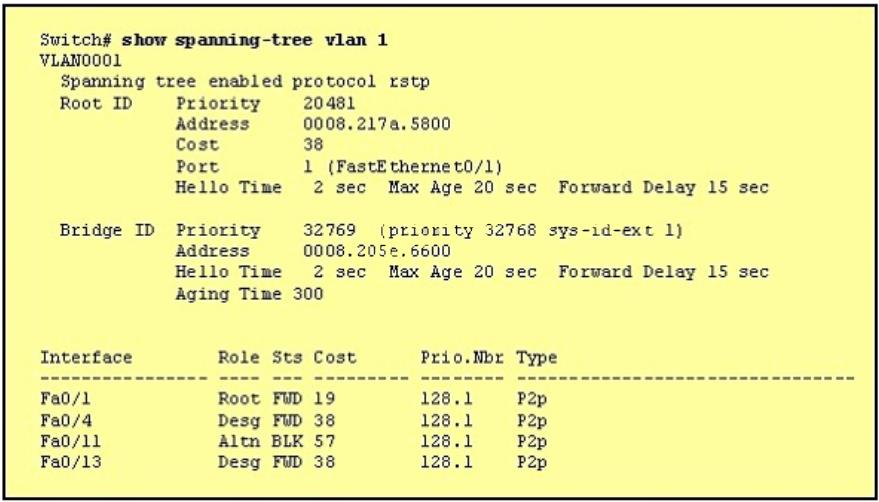
Why has this switch not been elected the root bridge for VLAN1?
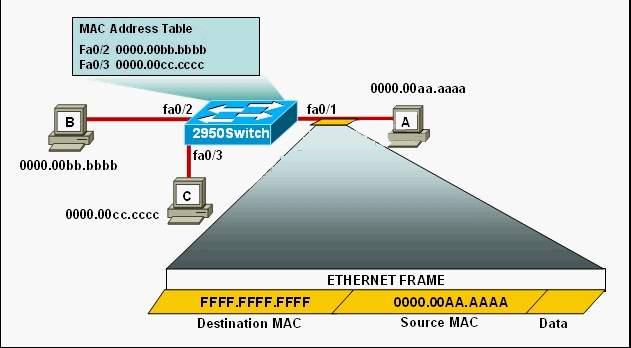
What two functions will occur when this frame is received by 2950Switch?
Refer to the exhibit.
The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)# switchport port-security
2950Switch(config-if)# switchport port-security mac-address sticky
2950Switch(config-if)# switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1.
What two functions will occur when this frame is received by 2950Switch? (Choose two.)
Which two are functional layers of a collapsed-core LAN design?
Which two are functional layers of a collapsed-core LAN design? (Choose two.)
Which two of these best describe the implementation of a WAN Backup design over the Internet?
Which two of these best describe the implementation of a WAN Backup design over the Internet?
(Choose two.)