What is the default encryption algorithm that is used by SRTP?
What is the default encryption algorithm that is used by SRTP?
Which three commands does Cisco recommend to use first when setting up phones for Cisco Unified Communications
Which three commands does Cisco recommend to use first when setting up phones for Cisco
Unified Communications Manager Express? (Choose three.)
Which of these is assigned to a phone or line to implement calling privileges?
Which of these is assigned to a phone or line to implement calling privileges?
Which Cisco Unified Border Element configuration supports H.323 protocol interworking and address hiding?
Which Cisco Unified Border Element configuration supports H.323 protocol interworking and
address hiding?
Which three factors must be considered when calculating the total bandwidth of a VoIP call, in order to avoid
Which three factors must be considered when calculating the total bandwidth of a VoIP call, in
order to avoid voice quality issues? (Choose three.)
Which two are advantages of a modular data center design?
Which two are advantages of a modular data center design? (Choose two.)
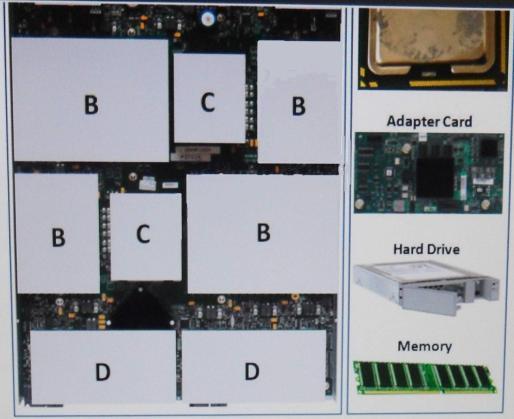
which empty component block?
What more can be done?
A Cisco Self-Defending Network has been installed, but DoS attacks are still being directed at ecommerce hosts. The connection rate at the Internet firewall was limited, but the problem persists.
What more can be done?
Which two commands or key sequences display a list of the available commands in the Cisco NXOS prompt UCS-swit
Which two commands or key sequences display a list of the available commands in the Cisco NXOS prompt UCS-switch (nxos) #? (Choose two)
Which two describe functions of the data center aggregation layer?
Which two describe functions of the data center aggregation layer? (Choose two.)