Which type of ephone-dn is configured for the two ephones that are shown?
which user took a specific action?
Which log file in Cisco UCS Manager contains information about which user took a specific action?
which three tools can be used to check the database replication status?
When a database replication issue is suspected, which three tools can be used to check the
database replication status? (Choose three.)
Which statement is true about system event logs?
Which statement is true about system event logs?
Which piece of information does the FSM provide?
Which piece of information does the FSM provide?
Which of these does not have an FSM associated with it?
Which of these does not have an FSM associated with it?
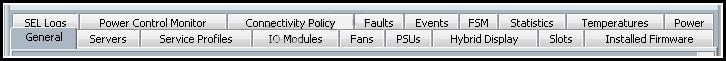
Which tab would be the most useful for troubleshooting a blade discovery problem?
Which of these reasons can cause intrasite calls within a Cisco Unified Communications Manager cluster to fail
Which of these reasons can cause intrasite calls within a Cisco Unified Communications Manager
cluster to fail?
which two of the following does the administrator need to verify to resolve this situation?
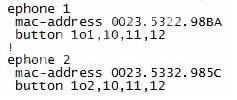
Refer to the exhibit.
A new Cisco Unified Communications Manager Express system has been deployed and the
technician is trying to add the first new IP phone to the system. The phone powers up, but it does
not register with the system. The technician has verified that the phone is getting the proper VLAN
information from Cisco Discovery Protocol. The phone is also getting the correct IP address and
TFTP server address from DHCP. The phone has been assigned to an ephone and the correct
MAC address is configured. With the information provided, which two of the following does the
administrator need to verify to resolve this situation? (Choose two.)
which two of these?
RBAC is a method of restricting access for a particular user on which two of these? (Choose two.)