which option must you configure to enable VLAN rewriting?
When deploying Cisco FirePOWER appliances, which option must you configure to
enable VLAN rewriting?
Which two methods are used to deploy transparent mode t…
Which two methods are used to deploy transparent mode traffic redirection? (Choose two)
Which option lists the minimum requirements to deploy a…
Which option lists the minimum requirements to deploy a managed device inline?
Which feature of the Cisco Hybrid Email Security servic…
Which feature of the Cisco Hybrid Email Security services enables you to create multiple
email senders on a single Cisco ESA?
what, is meant by simple custom detection?
Which Cisco AMP for Endpoints, what, is meant by simple custom detection?
which two interface settings are required when configur…
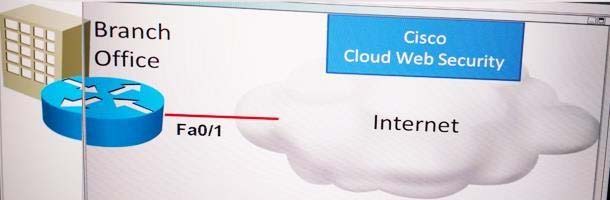
Your organization has subscribed to the Cisco Cloud Web Security (CWS) service. You
have been assigned the task of configuring the CWS connector on the ISR-G2 router at a
branch office. Details of the configuration requirements include:
. Content scanning should be enabled for traffic outbound from FastEthernet0/1
. Explicitly specify 8080 for both the http and the https ports
. The primary CWS proxy server is proxy-a.scansafe.net
. The secondary CWS proxy server is proxy-b.scansafe.net
. The unencrypted license key is 0123456789abcdef
. If the CWS proxy servers are not available. web traffic from the branch office should be
denied
. After configuration. use show commands to verify connectivity with the CWS service
and scan activity You can access the console of the ISR at the branch office using the icon
on the topology display. The enable password is Cisco!23
With Firepower Threat Defense, which two interface settings are required when
configuring a routed interface? (Choose two.)
Which interface type allows packets to be dropped?
Which interface type allows packets to be dropped?
Which type of policy do you configure if you want to lo…
Which type of policy do you configure if you want to look for a combination of events
using Boolean logic?
Which Cisco Advanced Malware protection for Endpoints d…
Which Cisco Advanced Malware protection for Endpoints deployment architecture is
designed to keep data within a network perimeter?
Which three statements about Cisco CWS are true’?
Which three statements about Cisco CWS are true’? (Choose three)