Which two types of rules are UNIX-only rules?
Which two types of rules are UNIX-only rules?
which configuration must be the exact reverse of the other IPsec peer?
You are the Cisco Configuration Assistant in your company, When you configure a site-to-site
IPsec VPN tunnel, which configuration must be the exact reverse of the other IPsec peer?
How do you make the ACL work?
You already created an ACL named ACLIN to permit traffic from certain Internet hosts to the web
server on your DMZ. How do you make the ACL work? Choose two.
Which type of tunnel mode can be used by DM VPN configuration on the tunnel interface?
Which type of tunnel mode can be used by DM VPN configuration on the tunnel interface?
CORRECT TEXT
Which two steps should the Cisco Adaptive Security Applicance take on HTTP traffic entering its outside interf
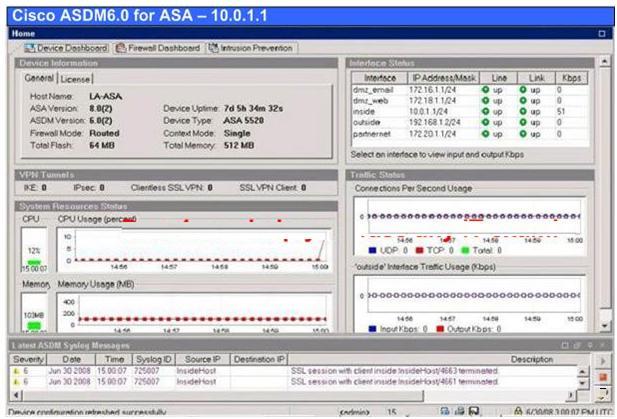
Modular Policy Framework provides a consistent and flexible way to configure security appliance
features in a manner similar to Cisco IOS software QoS CLI. Your company asked you to examine
the current Cisco Modular Policy Framework configurations on the LA-ASA Cisco Adaptive
Security Appliance (ASA) by use of the Cisco Adaptive Security Device Manager (ASDM).
Which two steps should the Cisco Adaptive Security Applicance take on HTTP traffic entering its
outside interface? (Choose two.)
Which one of the five phases of an attack attempts to become resident on a target?
Which one of the five phases of an attack attempts to become resident on a target?
Which of the following configures an authentication proxy rule for the IOS Firewall?
You are configuring the authentication feature on a new Company router. Which of the following
configures an authentication proxy rule for the IOS Firewall?
Which feature allows an administrator to edit the reachable subnets at both ends of the LAN-toLAN tunnel?
Which feature allows an administrator to edit the reachable subnets at both ends of the LAN-toLAN tunnel?