which function can be enabled by using the port-forward command?
While configuring Cisco IOS WebVPN, which function can be enabled by using the port-forward
command?
Which two impacts are of the policy map named PARTNERNET-POLICY on FTP traffic entering the partnernet interfa
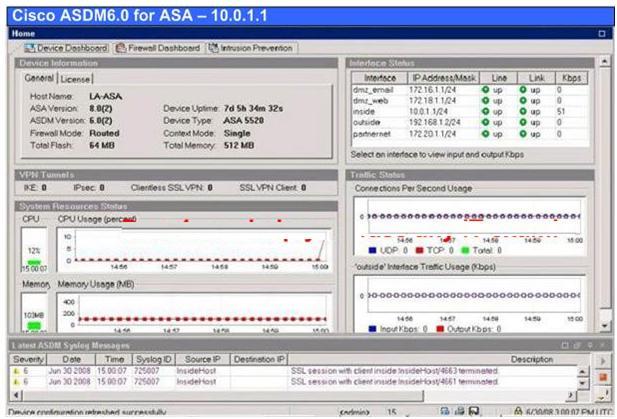
Modular Policy Framework provides a consistent and flexible way to configure security appliance
features in a manner similar to Cisco IOS software QoS CLI. Your company asked you to examine
the current Cisco Modular Policy Framework configurations on the LA-ASA Cisco Adaptive
Security Appliance (ASA) by use of the Cisco Adaptive Security Device Manager (ASDM).
Which two impacts are of the policy map named PARTNERNET-POLICY on FTP traffic entering
the partnernet interface?
how many half-open sessions need to be in the state table before CBAC will begin to delete the half-open sessi
By default, how many half-open sessions need to be in the state table before CBAC will begin to
delete the half-open sessions?
Which two attacks could an attacker use during the penetrate phase of an attack?
Which two attacks could an attacker use during the penetrate phase of an attack? (Choose two.)
Which two certificates need to be installed in the Cisco VPN 3000 Concentrator?
Which two certificates need to be installed in the Cisco VPN 3000 Concentrator? Choose two.
Which three statements accurately describe DMVPN configuration?
D4Which three statements accurately describe DMVPN configuration? (Choose three,)
What is the primary advantage of using Mode Configuration?
What is the primary advantage of using Mode Configuration?
What does authentication proxy on the Cisco IOS Firewall do?
The authentication proxy feature has been configured on one of the Company routers. What does
authentication proxy on the Cisco IOS Firewall do?
Which protocol is required for the administrative workstation to communicate with the CSA MC?
Which protocol is required for the administrative workstation to communicate with the CSA MC?
What is the reason that you want to configure VLANs on a security appliance interface?
What is the reason that you want to configure VLANs on a security appliance interface?