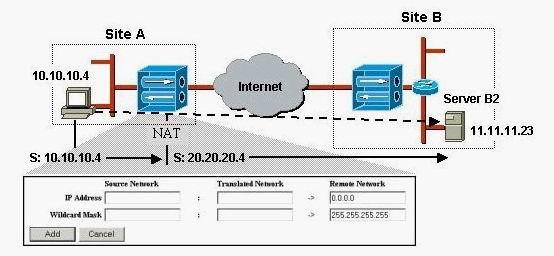
how are the translated network IP address and wildcard mask configured on the Concentrator?
Which option is correct about the output of the Cisco IOS IPS configuration displayed in the following exhibit
What is the purpose of the sniffer and protocol detection rule?
What is the purpose of the sniffer and protocol detection rule?
what is the minimum version of the PIX Firewall?
For the Cisco VPN Client to interoperate with a PIX Firewall, what is the minimum version of the
PIX Firewall?
How do you configure the CBAC global UDP idle session timeout?
You have been tasked with setting up a new router with CBAC. How do you configure the CBAC
global UDP idle session timeout?
Which three encapsulation types will be supported by the Cisco ASA security appliance for IPsec NAT transparen
Which three encapsulation types will be supported by the Cisco ASA security appliance for IPsec
NAT transparency? (Choose three.)
which traffic can be passed between the client PC and the Cisco Catalyst switch over the uncontrolled port?
While deploying S02.1X authentication on Cisco Catalyst switches, which traffic can be passed
between the client PC and the Cisco Catalyst switch over the uncontrolled port?
Which protocol should never be disabled on the CSA MC?
Which protocol should never be disabled on the CSA MC?
What are two purposes of the X.509 Certificate Serial Number?
What are two purposes of the X.509 Certificate Serial Number? Choose two.
which of the above mentioned commands?
The graphic shows a partial configuration. An account manager (AM) at a small site wants to
access the boston_sales.cisco.com server. The account manager knows the name, but not the IP
address of the server. The AM’s PC requests DNS resolution of the inside web server address
from a DNS server on an outside network. To enable the PIX Firewall to perform a DNS A record
translation correctly for the above mentioned application, the DNS key word should be added to
which of the above mentioned commands?