Which statement about intrusion detection in the PIX Firewall is true?
Which statement about intrusion detection in the PIX Firewall is true?
which corrective action should be configured or corrected for the VPN tunnel to come up properly?
Annie is a network administrator of her company. She is responsible for a Cisco ASA security
appliance. Using a valid identity certificate from her certificate authority, she has created the
necessary configuration for remote-access VPN tunnels by use of the IPsec VPN Wizard. When
she tests the remote-access VPN, the VPN tunnel does not come up. If the remote-access VPN
configuration created by the wizard is correct and valid certificates are being used by the Cisco
ASA security appliance and Cisco VPN Client, which corrective action should be configured or
corrected for the VPN tunnel to come up properly?
When should you use preconfigured application classes for application deployment investigation?
When should you use preconfigured application classes for application deployment investigation?
what three files are required?
To pre-configure a Cisco VPN client, what three files are required? Choose three.
Which of the following represents the behavior of the CBAC aggressive mode in a Cisco IOS firewall?
Which of the following represents the behavior of the CBAC aggressive mode in a Cisco IOS
firewall?
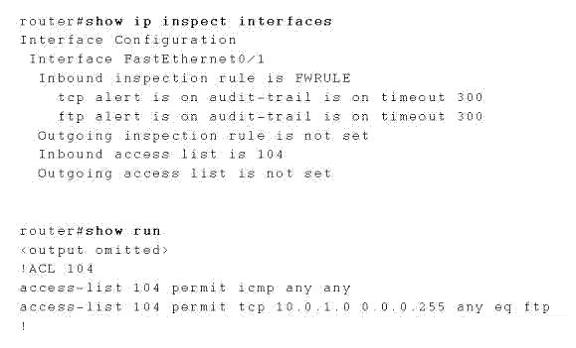
what could be a reason for users on the trusted inside networks not to be able to successfully establish outbo
You are in charge of Securing Networks Cisco Routers and Switches in your company Given that
the faO/1 interface is the trusted interface, what could be a reason for users on the trusted inside
networks not to be able to successfully establish outbound HTTP connections based on the
following configuration?
what will fail if the ip nhrp map multicast dynamic command is missing on the tunnel interface?
The Dynamic Multipoint VPN (DMVPN) feature allows users to better scale large and small IP
Security (IPsec) Virtual Private Networks (VPNs) by combining generic routing encapsulation
(GRE) tunnels, IPsec encryption, and Next Hop Resolution Protocol (NHRP).Referring to a
DMVPN hub router tunnel interface configuration, what will fail if the ip nhrp map multicast
dynamic command is missing on the tunnel interface?
Which two of the following file access rule criteria can you use to allow or deny the operations that the sele
Which two of the following file access rule criteria can you use to allow or deny the operations that
the selected applications can perform on files? (Choose two.)
What does Reverse Route Injection enable in this configuration?
Reverse route injection (RRI) is the ability for static routes to be automatically inserted into the
routing process for those networks and hosts protected by a remote tunnel endpoint. These
protected hosts and networks are known as remote proxy identities. Study the following exhibit
carefully. What does Reverse Route Injection enable in this configuration?
Which statement about authentication and the PIX Firewall is true?
Which statement about authentication and the PIX Firewall is true?