Match the ACS 4.0 component on the left to the correct function on the right.
what should be the next step after the PHDFs have been loaded?
When configuring FPM, what should be the next step after the PHDFs have been loaded?
How to handle FTP on the security appliance after this policy is applied?
You are the network security administrator for the P4S company. You create an FTP inspection
policy including the strict option, and it is applied to the outside interface of the corporate adaptive
security appliance. How to handle FTP on the security appliance after this policy is applied?
(Choose three.)
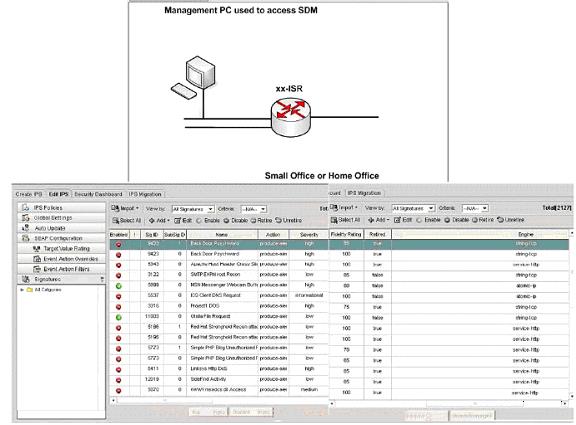
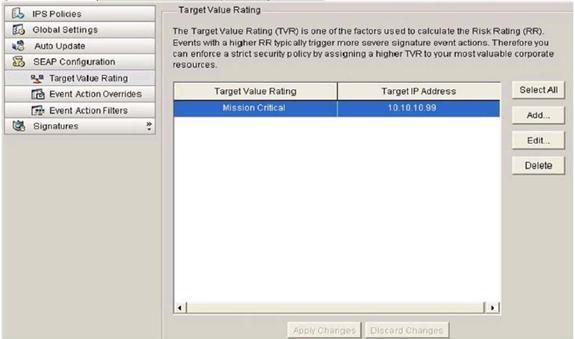
What is the Fidenlity Rating of the DDoSTrinoo IPS signature (signature ID 4608, subsignature-id 3)?
Why is the IPsec site-to-site VPN between Router A and Router B not working?
How many signatures are loaded?
Which type of VPN is considered an extension of the classic WAN network?
Which type of VPN is considered an extension of the classic WAN network?
how can you select a specific EAP type to use for 802.1x authentication?
If you enable all the authentication protocols under the Global Authentication Setup in Cisco ACS,
how can you select a specific EAP type to use for 802.1x authentication?
how are deny actions logged?
When you choose the Log All Deny Actions option within a group, how are deny actions logged?