Which three authentication methods are supported by Cisco Secure ACS?
Which three authentication methods are supported by Cisco Secure ACS? (Choose three.)
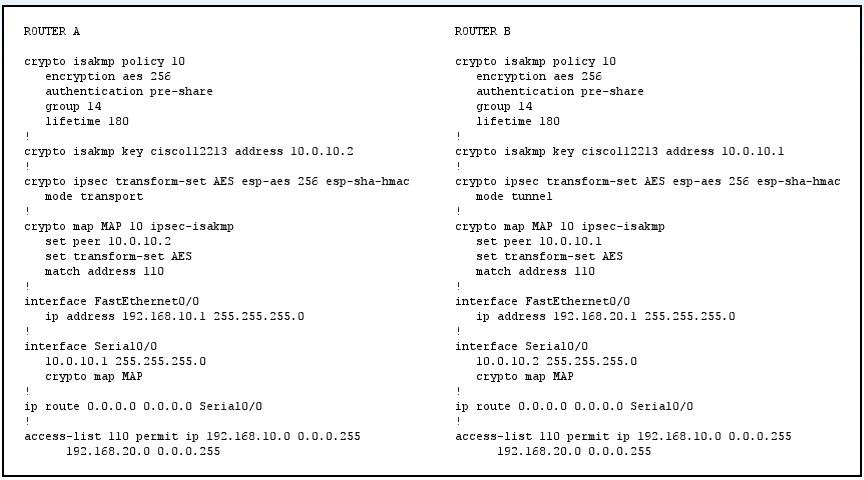
Which technology provides an automated digital certificate management system for use with IPsec?
Which technology provides an automated digital certificate management system for use with IPsec?
which three benefits to the customer?
The Worthington, Lane, Andrews and Newton manufacturing company has three facilities that are
located in the city of Columbia, South Carolina, with the corporate office located in downtown
Columbia. The R&D facility is located on the north side of the city 4 miles (6.4 km) from the
corporate office, and is leasing office space in a five-story building. The manufacturing facility is
located 6 miles (9.6 km) to the northwest of the corporate office and 2 miles (3.2 km) west of the
R&D facility. Users at the manufacturing plant require network connectivity for file sharing and emailing, while the users at the R&D facility require high-speed Internet access with the ability to
send large CAD drawings to the corporate office and large machine control files to the
manufacturing facility. Presently, the manufacturing facility is connected to the corporate office by
a 64-Kbps leased-line, and the R&D facility is connected to both the corporate office and the
manufacturing facility by a dedicated T1 line. The company plans to add a second line of
development at the R&D facility within the next 60 days. However, the current T1 lines are at a
constant 70-percent utilization rate. Currently, a T1 line costs US$750 per month for each line. The
current projected lead time for installation of additional lines is 90 days, if the current cable plant
will support it. A wireless bridging solution would provide which three benefits to the customer?
(Choose three.)
Which two IPsec protocols are used to protect data in motion?
Which two IPsec protocols are used to protect data in motion? (Choose two.)
Which two threats are detected by means of the Cisco Network Admission Control?
Which two threats are detected by means of the Cisco Network Admission Control? (Choose two.)
which protocol number does Encapsulating Security Payload operate?
On which protocol number does Encapsulating Security Payload operate?
how many users?
When using Cisco advanced feature set products, integrated guest access supports how many
users?
which protocol number does the authentication header operate?
On which protocol number does the authentication header operate?
which two authentication types?
The local authentication service on an autonomous access point supports which two
authentication types? (Choose two.)