What is used at the access layer to provide logical separation between the voice and data traffic?
What is used at the access layer to provide logical separation between the voice and data traffic?
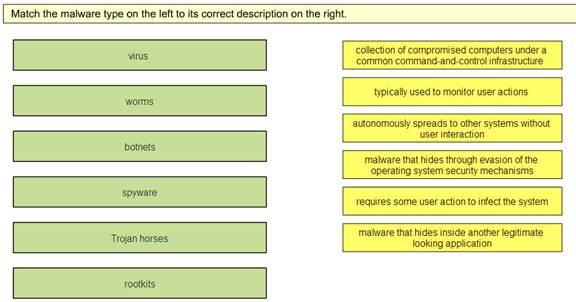
Match the malware type on the left to its correct description on the right.
Which authentication protocol can provide single sign-on (SSO) services?
Which authentication protocol can provide single sign-on (SSO) services?
Which solution stops new web threats the earliest?
Which solution stops new web threats the earliest?
Which essential element is needed to perform events analysis and correlation?
Which essential element is needed to perform events analysis and correlation?
Which three benefits does DMVPN offer?
Which three benefits does DMVPN offer? (Choose three.)
which three security controls?
Digital signatures can be used to provide which three security controls? (Choose three.)
What are the four main deployment options to consider when implementing Cisco NAC Appliance design?
What are the four main deployment options to consider when implementing Cisco NAC Appliance
design? (Choose four.)
Which additional security control can be used in multi-tier applications and multi-tier firewall designs…
Which additional security control can be used in multi-tier applications and multi-tier firewall
designs to force an attacker to compromise the exposed server before the attacker can attempt to
penetrate the more protected domains?
Which feature is used to inspect encrypted web traffic for malware?
Which feature is used to inspect encrypted web traffic for malware?