You have completed this exercise when you have configured and successfully tested…
SIMULATION
You are the network security engineer for the Secure-X network. The company has recently detected
Increase of traffic to malware Infected destinations. The Chief Security Officer deduced that some
PCs in the internal networks are infected with malware and communicate with malware infected
destinations.
The CSO has tasked you with enable Botnet traffic filter on the Cisco ASA to detect and deny further
connection attempts from infected PCs to malware destinations. You are also required to test your
configurations by initiating connections through the Cisco ASA and then display and observe the
Real-Time Log Viewer in ASDM.
To successfully complete this activity, you must perform the following tasks:
* Download the dynamic database and enable use of it.
• Enable the ASA to download of the dynamic database
• Enable the ASA to download of the dynamic database.
• Enable DNS snooping for existing DNS inspection service policy rules..
• Enable Botnet Traffic Filter classification on the outside interface for All Traffic.
• Configure the Botnet Traffic Filter to drop blacklisted traffic on the outside interface. Use the
default Threat Level settings
NOTE: The database files are stored in running memory; they are not stored in flash memory.
NOTE: DNS is enabled on the inside interface and set to the HQ-SRV (10.10.3.20).
NOTE: Not all ASDM screens are active for this exercise.
• Verify that the ASA indeed drops traffic to blacklisted destinations by doing the following:
• From the Employee PC, navigate to http://www.google.com to make sure that access to the
Internet is working.
• From the Employee PC, navigate to http://bot-sparta.no-ip.org. This destination is classified as
malware destination by the Cisco SIO database.
• From the Employee PC, navigate to http://superzarabotok-gid.ru/. This destination is classified as
malware destination by the Cisco SIO database.
• From Admin PC, launch ASDM to display and observe the Real-Time Log Viewer.
You have completed this exercise when you have configured and successfully tested Botnet traffic
filter on the Cisco ASA.
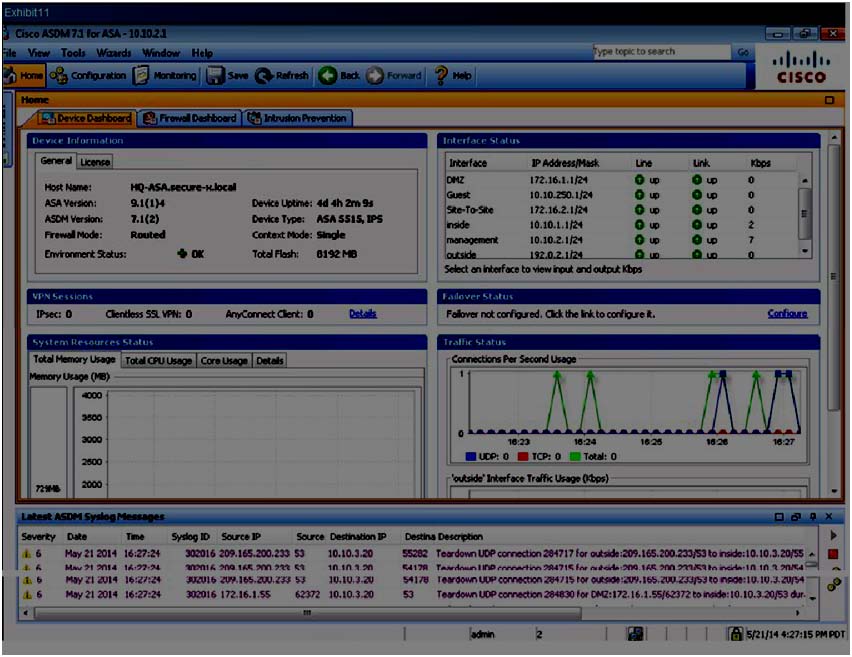
why isn’t the syslog server receiving any syslog messages?
what will happen if syslog server 10.10.2.40 fails?
Which statement is true of the logging configuration on the Cisco ASA?
Which three functions are executed using the Cisco TMS?
Which three functions are executed using the Cisco TMS? (Choose three.)
Which Cisco TMS extension integrates Cisco TMS with IBM Lotus Domino Server 7.0.x, 8.0.x, 8.5.x?
Which Cisco TMS extension integrates Cisco TMS with IBM Lotus Domino Server 7.0.x,
8.0.x, 8.5.x?
Which two prefixes does the event log use to identify changes to series of single instances?
In Cisco TMS, the conference control center shows event logs in instance basis. Which two
prefixes does the event log use to identify changes to series of single instances? (Choose
two.)
Which three functionalities can be performed by Cisco TMS?
Which three functionalities can be performed by Cisco TMS? (Choose three.)
Where do you navigate to within Cisco TMS to place a call?
Where do you navigate to within Cisco TMS to place a call?
Which two protocols allow Cisco TMS to manage an EX60 endpoint?
Which two protocols allow Cisco TMS to manage an EX60 endpoint? (Choose two.)