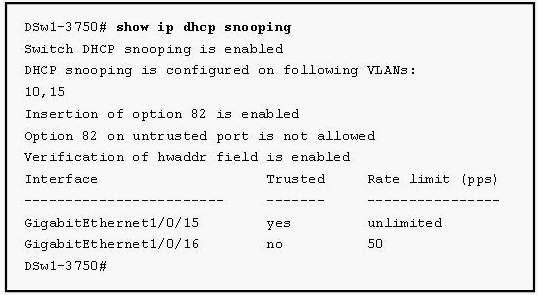
What type of attack is being defended against?
Which statement is true about the Forward Information Base (FIB) table?
Company has implemented numerous multilayer switches that utilize FIB tables. Which
statement is true about the Forward Information Base (FIB) table?
Which device should be used to accomplish this?
The Company network needs to pass traffic between VLANs. Which device should be used
to accomplish this?
what are some of the disadvantages of designing a router-on-stick configuration?
Inter-VLAN routing has been implemented in the Company network. In VLAN routing, what
are some of the disadvantages of designing a router-on-stick configuration? (Select three)
Which of the following could be used to provide a Layer 3 data path between separate VLANs?
Which of the following could be used to provide a Layer 3 data path between separate
VLANs? (Choose two.)
Which command would you use to configure a port to act as a routed interface?
You are configuring a Cisco multilayer switch for the Company network. Which command
would you use to configure a port to act as a routed interface?
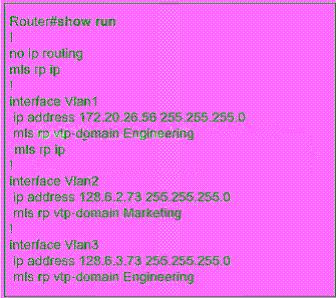
What could be the cause?
Which two statements about these attacks are true?
The Company security administrator is concerned with VLAN hopping based attacks. Which
two statements about these attacks are true? (Select two)
What is one method that can be used to do this?
The Company security administrator wants to prevent VLAN hopping on the network. What
is one method that can be used to do this?
Which two statements about VLAN hopping are true?
A hacker on the Company network is attempting to hop onto a different VLAN. Which two
statements about VLAN hopping are true? (Choose two)