Which two troubleshooting steps should be taken when Ci…
Which two troubleshooting steps should be taken when Cisco AnyConnect cannot establish an
IKEv2 connection, while SSL works fine? (Choose two.)
What could cause this issue?
What is the most likely cause of this problem?
The Cisco AnyConnect client is unable to download an updated user profile from the ASA headend
using IKEv2. What is the most likely cause of this problem?
What is the most possible cause of this problem?
The Cisco AnyConnect client fails to connect via IKEv2 but works with SSL. The following error
message is displayed:
“Login Denied, unauthorized connection mechanism, contact your
administrator”
What is the most possible cause of this problem?
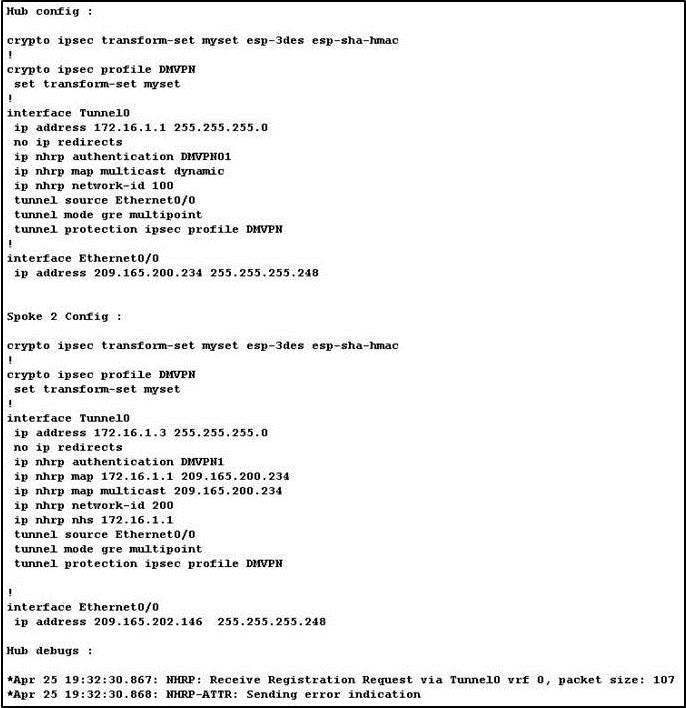
What is the problem?
What does this output suggest?
After completing a site-to-site VPN setup between two routers, application performance over the
tunnel is slow. You issue the show crypto ipsec sa command and see the following output. What
does this output suggest?
interfacE. Tunnel100
Crypto map tag: Tunnel100-head-0, local addr 10.10.10.10
protected vrF. (none)
local ident (addr/mask/prot/port): (10.10.10.10/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (10.20.20.20/255.255.255.255/47/0)
current_peer 209.165.200.230 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 34836, #pkts encrypt: 34836, #pkts digest: 34836
#pkts decaps: 26922, #pkts decrypt: 19211, #pkts verify: 19211
#pkts compresseD. 0, #pkts decompresseD. 0
#pkts not compresseD. 0, #pkts compr. faileD. 0
#pkts not decompresseD. 0, #pkts decompress faileD. 0
#send errors 0, #recv errors 0
Which adaptive security appliance command can be used t…
Which adaptive security appliance command can be used to see a generic framework of the
requirements for configuring a VPN tunnel between an adaptive security appliance and a Cisco
IOS router at a remote office?
What does this output suggest?
You are troubleshooting a site-to-site VPN issue where the tunnel is not establishing. After issuing
the debug crypto ipsec command on the headend router, you see the following output. What does
this output suggest?
1d00h: IPSec (validate_proposal): transform proposal
(port 3, trans 2, hmac_alg 2) not supported
1d00h: ISAKMP (0:2) : atts not acceptable. Next payload is 0
1d00h: ISAKMP (0:2) SA not acceptable
What does this output suggest?
You are troubleshooting a site-to-site VPN issue where the tunnel is not establishing. After issuing
the debug crypto isakmp command on the headend router, you see the following output. What does
this output suggest?
1d00h: ISAKMP (0:1): atts are not acceptable. Next payload is 0
1d00h: ISAKMP (0:1); no offers accepted!
1d00h: ISAKMP (0:1): SA not acceptable!
1d00h: %CRYPTO-6-IKMP_MODE_FAILURE.
Processing of Main Mode failed with peer at 10.10.10.10
which that route originated?
A rogue static route is installed in the routing table of a Cisco FlexVPN and is causing traffic to be
blackholed. Which command should be used to identify the peer from which that route originated?