Which two methods can be used to challenge the identity of an IP phone from a Cisco Unified CallManager server
Which two methods can be used to challenge the identity of an IP phone from a Cisco Unified
CallManager server? (Choose two.)
which settings should be set on a Cisco ip phone that is placed in a public Space like a lobby?
At the very minimum which settings should be set on a Cisco ip phone that is placed in a public
Space like a lobby? (Choose two)
Which two qualities of PKI key exchange overcome asymmetric cryptography scalability issues?
Which two qualities of PKI key exchange overcome asymmetric cryptography scalability issues?
(Choose two.)
which situation would a device be allowed to use these devices?
If there are media resources that are not assigned to a Media Resource Group, in which situation
would a device be allowed to use these devices?
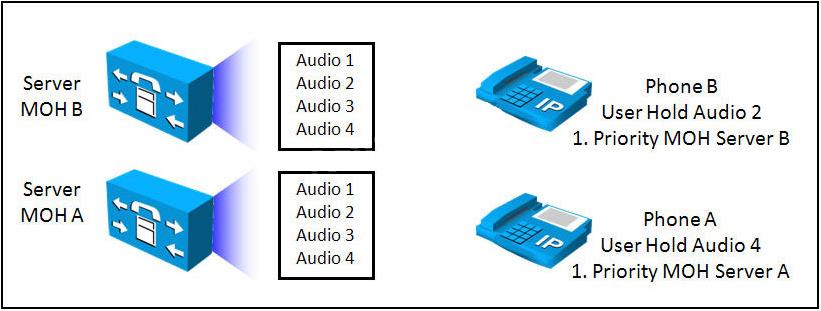
which server it will be played?
Which four of these media resources can be hardware-based in Cisco Unified Communication Manager?
Which four of these media resources can be hardware-based in Cisco Unified Communication
Manager?
Where is toll-fraud prevention configured in CUCM?
Where is toll-fraud prevention configured in CUCM?
Which three of These Media Resources Can Be based hardware?
Which three of These Media Resources Can Be based hardware?
Which component is required when deploying Music on Hold with recorded or live audio?
Which component is required when deploying Music on Hold with recorded or live audio?