According to the Cisco Network Foundation Protection architecture, which security feature should be applied at
According to the Cisco Network Foundation Protection architecture, which security feature should be applied at the access layer?
When a Cisco WAE that was optimizing connections fails, which two symptoms will appear in a TCP trace? (Choose
When a Cisco WAE that was optimizing connections fails, which two symptoms will appear in a TCP trace? (Choose two.)
How many RUs will it need?
Your customer is planning to deploy a pair of clustered Cisco WAE-7326 appliances in its data center. How many RUs will it need?
In a WAAS Application Traffic Policy, what are three valid match conditions for traffic classifiers? (Choose t
In a WAAS Application Traffic Policy, what are three valid match conditions for traffic classifiers? (Choose three.)
Which WCCPv2 interception configuration should you apply to the Serial0 interface?
Which description is correct about Cisco WAAS Transport Flow Optimization?
Which description is correct about Cisco WAAS Transport Flow Optimization?
What should you do?
domain .com has configured each Cisco WAE to belong to multiple device groups for monitoring purposes. However, the customer wants to ensure that the policies are applied to the device from one specific device group. What should you do?
With Cisco WAAS, which two WCCPv2 service groups are used to make up the TCP Promiscuous service group? (Choos
With Cisco WAAS, which two WCCPv2 service groups are used to make up the TCP Promiscuous service group? (Choose two.)
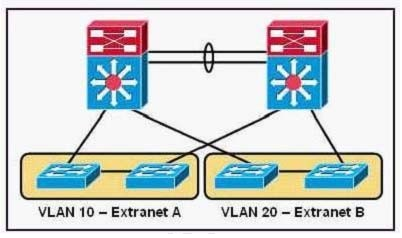
Which security feature would you use to prevent a worm outbreak in Extranet A from crossing into Extranet B?
At which point will the Cisco WAE start to pass through traffic because of overload?
The Cisco WAE Appliances provide a unified platform for hosting Cisco application acceleration and WAN optimization solutions. At which point will the Cisco WAE start to pass through traffic because of overload?