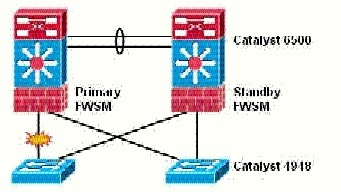
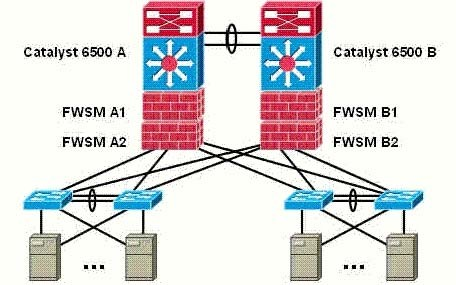
Which Layer 2 topology can cause a break in connectivity between the FWSMs?
Which of these is least important when determining how many users a NAS can support?
You are the Cisco Network Designer. Which of these is least important when determining how many users a NAS can support?
Which design should you avoid?
Your customer plans to deploy FWSM and IDSM modules in the aggregation layer. Which design should you avoid?
if Acme Nutrition plans for 20 percent growth in facilities, how many Class C subnets will the district sales
Acme Nutrition manufactures a wide variety of vitamin supplements. It has a single manufacturing facility with 3 regional warehouses and 16 district sales offices. Currently the manufacturing facility requires 210 IP addresses; each warehouse requires 51 IP addresses; each district sales office requires 11 IP addresses; and the IP WAN requires 38 IP addresses. if Acme Nutrition plans for 20 percent growth in facilities, how many Class C subnets will the district sales offices require?
Which QoS mechanism can you implement to improve the network response time?
Users at the Charleville Company began experiencing high network delays when Internet connectivity was enabled for all users. After investigating the traffic flow, you determine that peer- to-peer traffic from a music download site is consuming a large amount of bandwidth. Which QoS mechanism can you implement to improve the network response time?
Which three of the following service modules can be deployed in redundant pairs with active/active failover? (
Which three of the following service modules can be deployed in redundant pairs with active/active failover? (Choose three.)
Which two of these key fields are used to identify a flow in a traditional NetFlow implementation? (Choose two
Which two of these key fields are used to identify a flow in a traditional NetFlow implementation? (Choose two.)
Which two areas of security would you advise the company to strengthen? (Choose two
The Schuyler and Livingston Iron Works has been working on getting its network security under control. It has set up VPN with IPSec links to its suppliers. It has installed network vulnerability scanners to proactively identify areas of weakness, and it monitors and responds to security events as they occur. It also employs extensive access control lists, stateful firewall implementations, and dedicated firewall appliances. The company has been growing very fast lately and wants to make sure it is up to date on security measures. Which two areas of security would you advise the company to strengthen? (Choose two.)
Which change might prevent this problem?
Which VPN topology should you recommend?
You are the network consultant from Cisco.com.Your customer has eight sites and will add in the future.
Branch site to branch site traffic is approaching 30 percent. The customer’s goals are to make it easier to add branch sites in the future and to reduce traffic through the hub. Which VPN topology should you recommend?