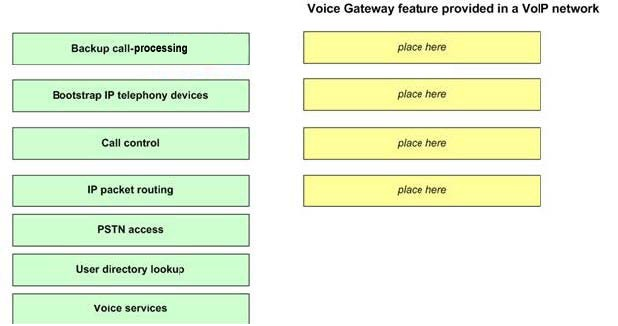
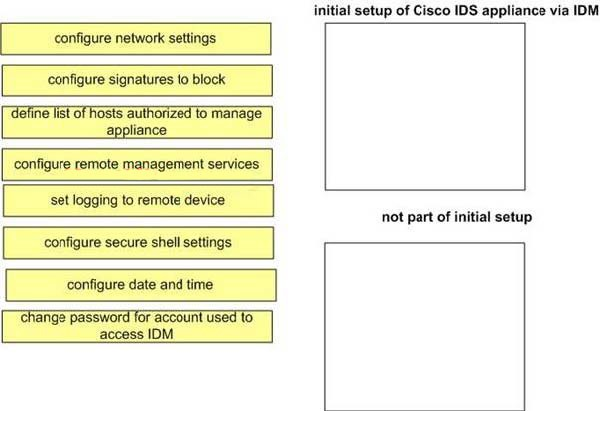
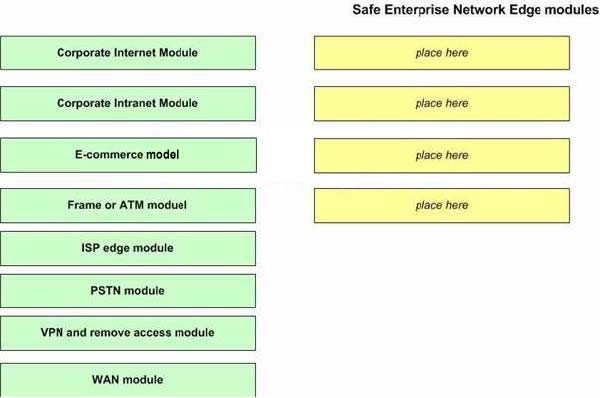
DRAG DROP
The IPSec receiver can detect and reject replayed packets.
The IPSec receiver (the one who receives the IPSec packets) can detect and reject replayed packets.
They should use … to mitigate against unauthorized access.
In the SAFE SMR, if the remote users who do not want to establish VPN tunnel when connected to the Internet, they should use ____________ to mitigate against unauthorized access.
Choose the tasks required for initial setup of the Cisco appliance via IDM.
You are designing an e-Commerce module, which routing statement is correct?
You are the Cisco Network Designer in Cisco.com. You are designing an e-Commerce module, which routing statement is correct?
Place them under SAFE Enterprise Network Edge modules
Choose the correct statement
The structure of Campus module in SAFE medium architecture may be altered. Choose the correct statement.
What can mitigate the chance of a department accessing confidential information
What can mitigate the chance of a department accessing confidential information on another department’s server through the use of access control in the SAFE SMR midsize network design midsize network campus module?
What type of threat consists mainly of random hackers
The security team at Certkiller Inc. is working on securing the network by understanding the type of threats. What type of threat consists mainly of random hackers using various common tools (such as malicious shell scripts, password crackers, credit card number generators, and dialer daemons)?
Following termination of the VPN tunnel, traffic is sent through:
In the corporate Internet module of SAFE SMR midsize network design, following termination of the VPN tunnel, traffic is sent through: