Drag Drop
Choose the true statements regarding IP spoofing attack and DoS attack
Choose the true statements regarding IP spoofing attack and DoS attack. (Choose all that apply)
Which action will you take to enable
Cisco Security MARS combines network intelligence, context correlation, vector analysis, anomaly detection, hotspot identification, and automated mitigation capabilities. Which action will you take to enable the Cisco Security MARS appliance to ignore false-positive events by either dropping the events completely, or by just logging them to the database?
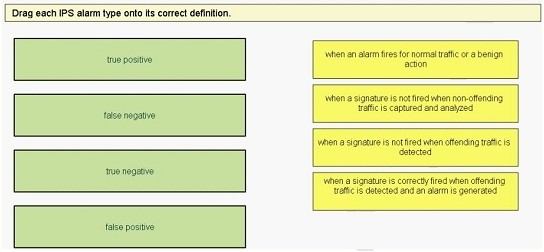
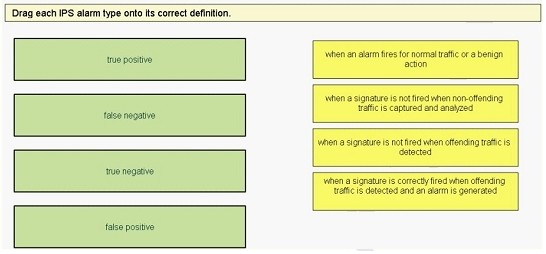
Drag Drop
The IPSec receiver (the one who receives the IPSec packets) can detect and reject replayed packets.
The IPSec receiver (the one who receives the IPSec packets) can detect and reject replayed packets.
This program does something undocumented which the programmer intended,
This program does something undocumented which the programmer intended, but that the user would not approve of if he or she knew about it.
On Cisco routers, which two methods can be used to secure privileged mode access?
On Cisco routers, which two methods can be used to secure privileged mode
access? (Choose two.)
Use the following values as necessary:
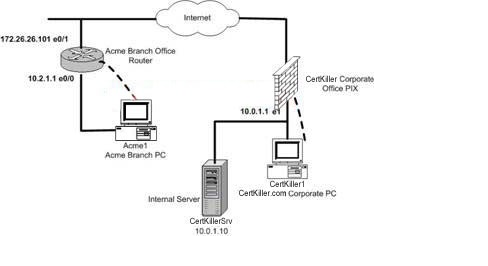
You are the network security administrator for the German company Certkiller Inc. Certkiller Inc. has recently acquired Acme, a small company in another country in Europe, and wants you to start creating a VPN tunnel over the Internet from the outside interface of the Certkiller ‘s corporate PIX Firewall to the outside interface of Acme’s branch office router using pre-shared keys. IKE has already been enabled on both devices. First configure the pre-shared key on each device and then configure the IKE parameters on each device. Use the following values as necessary:
Parameter Value
policy priority number 20
encryption algorithm 3des
has algorithm md5
authentication method pre-share
Diffie-Hellman Group ID 2
SA lifetime 83000
Pre-shared Key my Certkiller
Transform Set Name Certkiller set
ISAKMP Identity Type IP address
PIX Firewall Outside Interface Address 192.168.1.2 Branch Office Outside Interface 172.26.26.101
Crypto Map Name Certkiller map
Netmask 255.255.255.0
1. IPSec parameters are not configured, should not be configured, and consequently the tunnel will not be established.
The Router and PIX have been configured with the following specifications:
Acme Branch Office Routerg
Name: Certkiller 2
E0/0 : 10.2.1.1/24
E0/1 : 172.26.26.101/24
Enable Password: Certkiller
Corporate Office PIX
Name: Certkiller 1
E0 : 192.168.1.2/24
E1 : 10.0.1.1/24
Enable password: Certkiller
Click on the picture of the host connected to a router by a serial console cable.
IPSec tunnel mode can only be used when the datagrams are:
IPSec tunnel mode can only be used when the datagrams are:
A network vulnerability scanner is part of which critical element of network and system security?
A network vulnerability scanner is part of which critical element of network and system security?