In which access mode has this NAS been configured to operate?
You are the Cisco Network Designer in Cisco.com. In your company site, a NAS is both physically and logically in the traffic path. The NAS identifies clients solely based on their MAC addresses. In which access mode has this NAS been configured to operate?
Drag the item on the left to the correct table it pertains to on the right?
DRAG DROP
Drag and drop the proper keywords to complete the command that will create a static route based upon the following. Destination network = 10.0.0.0/8, Next hop = 10.10.212.2, Output interface = serial 0/0, VPN = RED ip route [k1] RED [k2] [k3] [K4] [K5]
Drag the item on the left to the correct table it pertains to on the right?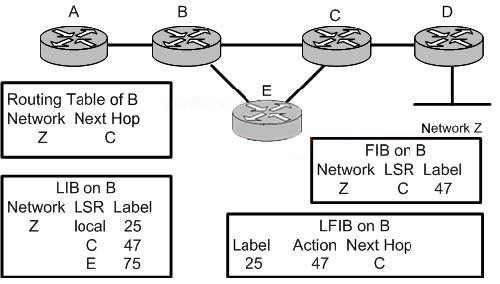
A Unified Communications Certificate is used on the Cisco ASA appliance to support which option?
A Unified Communications Certificate is used on the Cisco ASA appliance to support which
option?
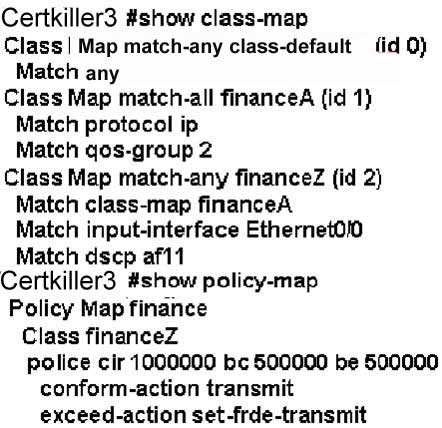
Which traffic will have Frame Relay DE bit set
What is a troubleshooting step that you should perform to determine the cause of the access problem?
You are the network security administrator. You receive a call from a user stating that he cannot
log onto the network. In the process of troubleshooting, you determine that this user is accessing
the network via certificate-based Cisco AnyConnect SSL VPN.
What is a troubleshooting step that you should perform to determine the cause of the access
problem?
Your trainee asks you why. (Select three.)
You work as a network administrator at Certkiller .com. You have deployed link efficiency mechanisms on a WAN Link. Your trainee asks you why. (Select three.)
which type of VPN tunneling should you use to allow the VPN traffic
When attempting to tunnel FTP traffic through a stateful firewall that might be performing NAT or
PAT, which type of VPN tunneling should you use to allow the VPN traffic through the stateful
firewall?
Name two sensitivities that Voice traffic has that data traffic is not necessarily affected by. (Choose two)
Name two sensitivities that Voice traffic has that data traffic is not necessarily affected by. (Choose two)
Where is the correct place to tune the IPsec policy parameters in Cisco ASDM?
After adding a remote-access IPsec tunnel via the VPN wizard, an administrator needs to tune the
IPsec policy parameters. Where is the correct place to tune the IPsec policy parameters in Cisco
ASDM?
Which statement is correct concerning the SSL VPN authorization process?
Authorization of a clientless SSL VPN defines the actions that a user may perform within a
clientless SSL VPN session. Which statement is correct concerning the SSL VPN authorization
process?