Which statement correctly describes the keyswitch model of deployment for call processing?
Which statement correctly describes the keyswitch model of deployment for call processing?
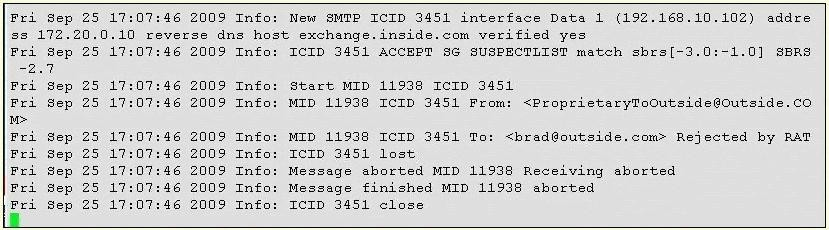
According to the mail log, what is the most likely problem?
Which three methods will do this? (Choose three
IPAS is enabled for all inbound mail but you want to bypass Spam checking for messages from cisco.com. Which three methods will do this? (Choose three.)
What are two of the implementation ratings found in the SBR Value Assessment? (Choose two
What are two of the implementation ratings found in the SBR Value Assessment? (Choose two.)
How many voice expansion slots are available on the UC520?
How many voice expansion slots are available on the UC520?
What is the best way to create a support ticket?
What is the best way to create a support ticket?
Which 2 benefits will a client see from adding a wireless lan controller to their SBCS? Select two
Which 2 benefits will a client see from adding a wireless lan controller to their SBCS? Select two.
Which of the following devices cannot support NIC Pairing?
Which of the following devices cannot support NIC Pairing?
What are two benefits for prospects, derived from the Cisco SBR methodology? (Choose two
What are two benefits for prospects, derived from the Cisco SBR methodology? (Choose two.)
After installing a certificate for TLS, where would you enable outbound TLS connections?
After installing a certificate for TLS, where would you enable outbound TLS connections?
22