What of the following statements that describe Diffie Hellman Key exchange are correct?
What of the following statements that describe Diffie Hellman Key exchange are correct? (Choose
4)
Which access methods can CS-MARS use to get configuration information from an Adaptive Security Appliance (ASA
Which access methods can CS-MARS use to get configuration information from an Adaptive Security Appliance (ASA)? (Choose 2)
which two Catalyst security features?
ARP cache poisoning can be best prevented by using which two Catalyst security features? (Choose two.)
what is causing the IKE Main Mode failure?
Referring to the debug output shown below, what is causing the IKE Main Mode failure?
1d00h: ISAKMP (0:1): atts are not acceptable. Next payload is 0
1d00h: ISAKMP (0:1): no offers accepted!
1d00h: ISAKMP (0:1): SA not acceptable!
1d00h: %CRYPTO-6-IKMP_MODE_FAILURE: Processing of Main Mode failed with peer at 150.150.150.1
which of the following would be a probable cause?
When an IPS device in single interface VLAN-pairing mode fires a signature from the normalizer engine and TCP-based packets are dropped, which of the following would be a probable cause?
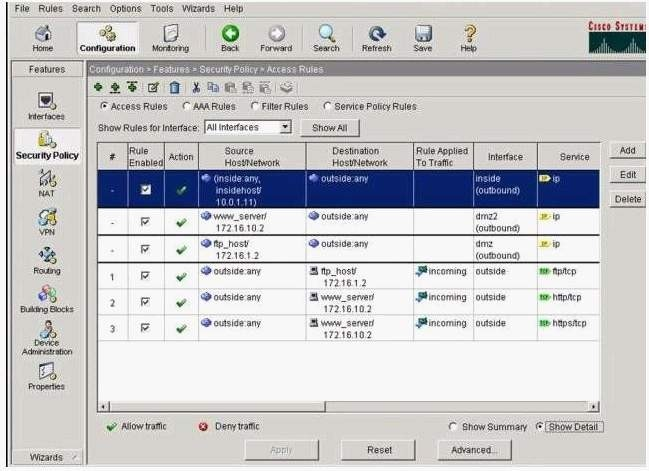
which of the following traffic is permitted based on the current Access Rules?
CSA protects your host by:
CSA protects your host by:
What is the most likely cause of this problem?
The key lengths for DES and 3DES, respectively, are:
The key lengths for DES and 3DES, respectively, are:
Which of the following are valid RADIUS packet flows’C indicates the user (such as a wireless laptop), N
Which of the following are valid RADIUS packet flows’C indicates the user (such as a wireless laptop), N indicates the NAS, and S indicates an ACS Server(Choose 2)