Which operational function within the FWSM handles this issue?
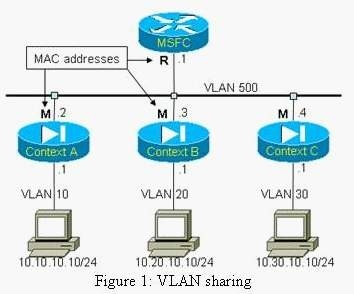
Figure 1 represents 3 security contexts all sharing a common VLAN (500)-a single IP subnet corresponds to that VLAN.This is equivalent to connecting three security appliances using an Ethernet switch.A property of the FWSM makes all interfaces across the entire module use only one global MAC address (‘M’ in Figure 1).This is usually not a problem, until multiple contexts start sharing an interface.Which operational function within the FWSM handles this issue?
Which two steps does a receiver perform to validate a message using HMAC?
Which two steps does a receiver perform to validate a message using HMAC? (Choose two.)
which one of the following is NOT a required step?
When enrolling a Cisco IOS router to a CA server using the SCEP protocol, which one of the following is NOT a required step?
which packet will be permitted by ACL 101?
which two statements are correct?
Which one of the following is NOT a supported IKE attribute?
Which one of the following is NOT a supported IKE attribute?
In an L2TP voluntary tunneling scenario, the VPDN tunel is terminated between:
In an L2TP voluntary tunneling scenario, the VPDN tunel is terminated between:
which statements are true?
which IOS feature to accomplish anomaly detection?
CS-MARS works with which IOS feature to accomplish anomaly detection?
which type of attacks?
RFC 2827 ingress filtering is used to help prevent which type of attacks?