what is the expected behavior when User_A attempts to edit.D:word.doc?
User_A and User_B are logged into Windows NT Workstation Host_A and Host_B respectively.
All users are logged in to the domain”CORP”.
All users run a logon script with the following line: “net useD:\CORPSVRdata”
– User_A and User_B are both members of the local group “USERS”.
– Local group “USERS” is includes in global group “DOMAIN USERS”.
– All users, hosts, and groups are in the domain “CORP”.
– The directory \CORPSVRdata has the share permission for local group “USERS” set to “No Access”.
– The Microsoft Word document \CORPSVRdataword.doc has file permissions for local group
“USERS” set to “Full Control”.
– The Microsoft Word document \CORPSVRdataword.doc is owned by User_B. Given this scenario on a
Windows NT 4.0 network, what is the expected behavior when User_A attempts to edit
D:word.doc?
what can be diagnosed as the biggest potential problem?
OSPF is defined on a Frame Relay interface providing point-to-multipoint connections. The remote neighbors can reach this central site, but are complaining of routing failures between each of the remote sites. The central router has all the routes for each remote site. Based on this information, what can be diagnosed as the biggest potential problem?
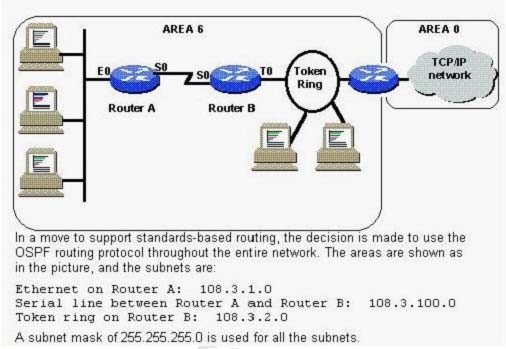
How should OSPF be configured on Router B?
How can this Java filter be circumvented?
Some packet filtering implementations block Java by finding the magic number 0xCAFEBABE at the beginning of documents returned via HTTP.How can this Java filter be circumvented?
Which response would NOT be preferred by an experienced Security Manager?
A remote user tries to login to a secure network using Telnet, but accidentally types in an invalid username or password. Which response would NOT be preferred by an experienced Security Manager? (Multiple answer)
Which of the following statements regarding Routing Information Protocol (RIP) is valid?
Which of the following statements regarding Routing Information Protocol (RIP) is valid?
what is the expected result?
When an IPSec authentication header (AH) is used in conjunction with NAT on the same IPSec endpoint, what is the expected result?
what will happen when someone Telnets into the router?
Exhibit:
aaa authentication login default local tacacs
aaa authorization exec default tacacs
aaa authentication login vty tacacs local
aaa authorization exec vty tacacs if-authenticated username abc password xuz
line vty 0 4
exec-timeout 0 0If a router running IOS 11.3 is configured as shown in the TACACS server is down, what will happen when someone Telnets into the router?
A RARP is sent:
A RARP is sent:
what concept?
In the realm of email security, “message repudiation” refers to what concept?