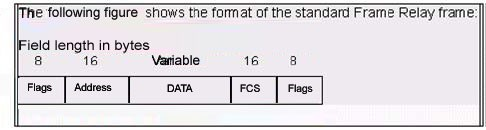
The user must be
When a proxy requires NTLM Authentication from a user and the system administrator does not want an authentication window to come up on the browser for the user to authenticate. The user must be:
You work as a network engineer at domain .com Study the exhibit carefully
In ATM:
In ATM:
Router A to prevent workstation Router 1 from overrunning the access port on Router B?
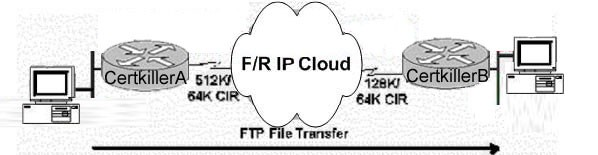
Exhibit
You work as a network engineer at Domain.com. Router Certkiller A has a 512K-access port into the frame relay cloud. Router Certkiller B has 128K-access port into the frame relay cloud. The two routers are connected with symmetrical PVCs that are configured for 64K committed information rate (CIR). What Frame Relay Traffic Shaping map-class sub-command should be entered on Router Certkiller A to prevent workstation Certkiller 1 from overrunning the access port on Router Certkiller B?
what devices resend packets that do not transmit correctly?
In Frame Relay, what devices resend packets that do not transmit correctly?
Unlike X25 Frame Relay is considered an unacknowledged protocol Why?
Unlike X.25, Frame Relay is considered an “unacknowledged” protocol. Why?
The Backup DIS is called?
To eliminate the need for adjacent routers on broadcast networks to form n(n-1)/2 adjacencies, IS-IS defines a pseudonode or Designated Intermediate System, DIS. All routers on the broadcast medium form an adjacency with the DIS. The Backup DIS is called…?
What statement is correct regarding Virtual LANs (VLANs)?
What statement is correct regarding Virtual LANs (VLANs)?
Which condition is required?
Which protocols are used to authenticate users?
Which protocols are used to authenticate users?