Which option is an important factor to consider in your implementation?
You have been tasked by your manager to implement syslog in your network. Which option is an important factor to consider in your implementation?
Which statement about an access control list that is applied to a router interface is true?
Which statement about an access control list that is applied to a router interface is true?
Which type of Cisco ASA access list entry can be configured to match multiple entries in a single statement?
Which type of Cisco ASA access list entry can be configured to match multiple entries in a single statement?
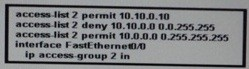
Which statement about this partial CLI configuration of an access control list is true?
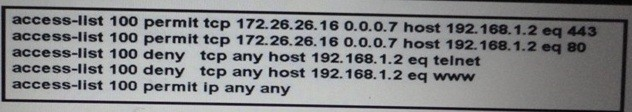
Which traffic is permitted by this ACL?
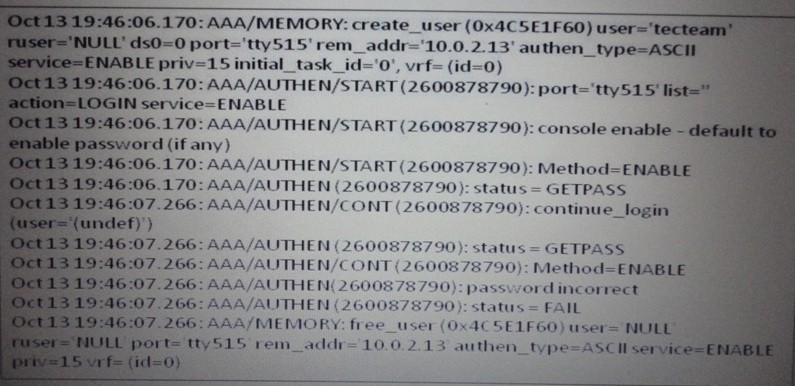
Which statement about this output is true?
Which two characteristics of the TACACS+ protocol are true?
Which two characteristics of the TACACS+ protocol are true? (Choose two.)
which two authentication methods should be used as the final method to ensure that the administrator can still
When AAA login authentication is configured on Cisco routers, which two authentication methods should be used as the final method to ensure that the administrator can still log in to the router in case the external AAA server fails? (Choose two.)
When executing the following show mpls l2transport vc detail command
When executing the following show mpls l2transport vc detail command, you notice the link does not come up. Choose the most likely cause.
PE#sho mpls l2transport vc detail
Local interface: Et0/0 up, line protocol up, Ethernet up
Destination address: 172.168.1.102, VC ID: 100, VC status: down Preferred path: not configured
Default path: active
Tunnel label: 16, next hop point2point
Output interface: Se5/0, imposed label stack {16 16}
Create time: 00:18:10, last status
change time: 00:03:51
Signaling protocol: LDP, peer 172.168.1.102:0 up
MPLS VC labels: local 16, remote 16
Group ID: local 0, remote 0
MTU: local 1500, remote unknown
Remote interface description:
Sequencing: receive disabled, send disabled
VC statistics:
packet totals: receive 0, send 0
byte totals: receive 0, send 0
packet drops: receive 0, send 78
Which protocols can be used to authenticate media-level access control
Which protocols can be used to authenticate media-level access control, offer the capability to permit or deny network connectivity, control VLAN access, and apply traffic policy, based upon user or machine identity?